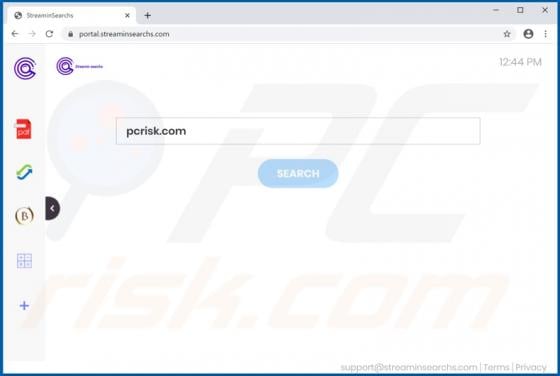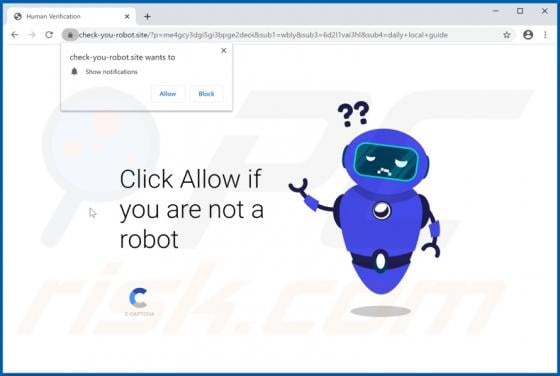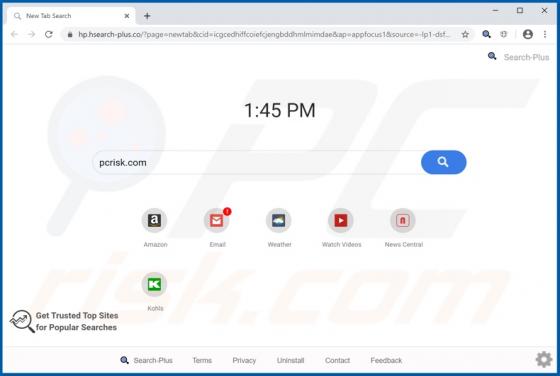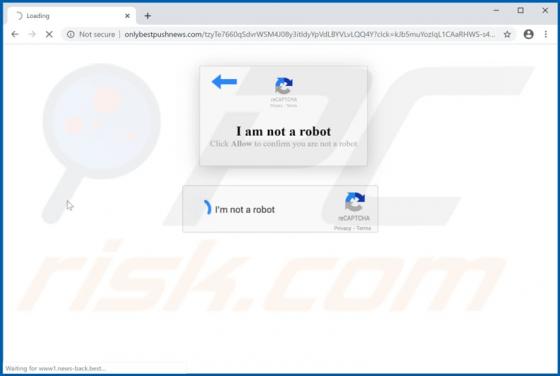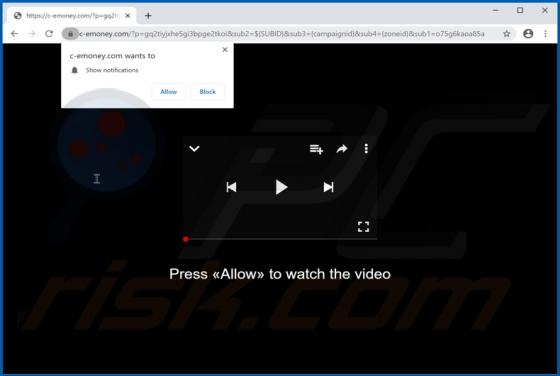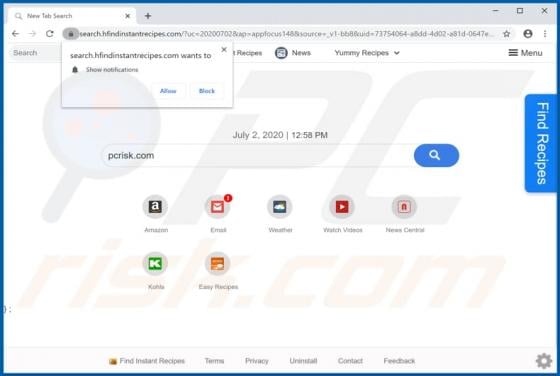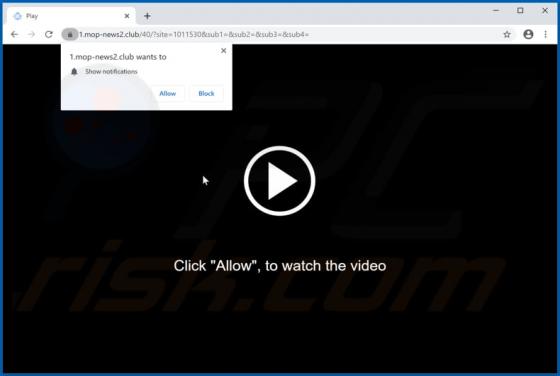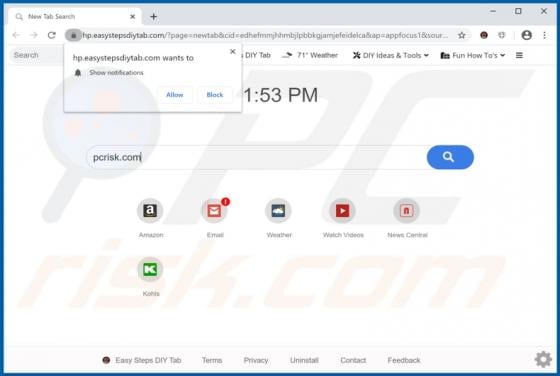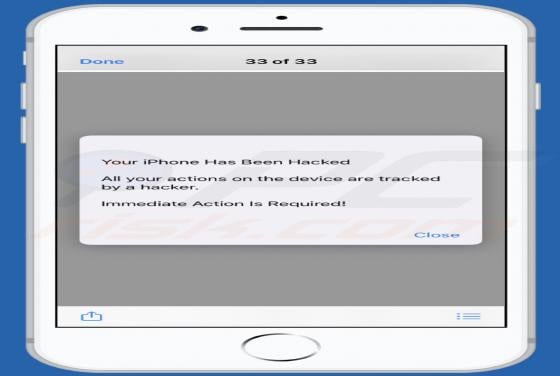
Your iPhone Has Been Hacked POP-UP Scam (Mac)
"Your iPhone Has Been Hacked" is a scam promoted by deceptive websites. As the title implies, the scheme claims that users' devices have been compromised and were accessed without authorization. "Your iPhone Has Been Hacked" also promotes other scams, which endorse untrusted and possibly malicio