How to remove the "NATIONAL SECURITY BUREAU" screen-locking message
RansomwareAlso Known As: NATIONAL SECURITY BUREAU malware
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "NATIONAL SECURITY BUREAU"?
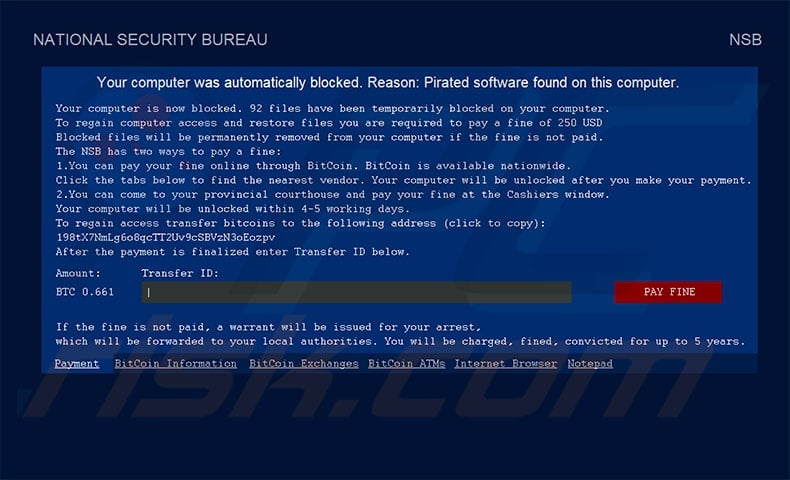
NATIONAL SECURITY BUREAU is malware designed to lock the computer screen and display a message stating that the system, together with a number of files, has been blocked, since 'pirated software' was found on the computer. Users are encouraged to pay a fine.
This malware infection is very similar to FBI Cybercrime Division Virus, FBI Virus - Your Computer Has Been Locked, and many others.
NATIONAL SECURITY BUREAU malware overview
The message states that use of pirated software has been detected and that the user will be arrested and sentenced up to five years if he/she does not pay a fine. The lock screen displays the title "NATIONAL SECURITY BUREAU", which makes the entire site look even more believable.
To avoid being convicted, users are encouraged to pay a fine of $250 or .661 Bitcoin (currently equivalent to ~$5300). Be aware that this is a scam. Firstly, there are several agencies with the name "NATIONAL SECURITY BUREAU", all of which are located in different countries (full list here). None is responsible for finding people who use 'cracked' applications.
Even if they were, they would certainly not lock computer screens and remotely ask users to pay fines using cryptocurrencies. Cyber criminals attempt to extort money from unsuspecting users. Note that, although NATIONAL SECURITY BUREAU claims to block data, it does not perform this function.
The message states that the fine is equivalent to $250, and yet requests a payment of .661 Bitcoin (which is currently equivalent to ~$5300).
Therefore, this malware has either been developed in 2015-2016 (and only recently went public) or developers have simply calculated incorrectly. In any case, the ransom (also known as a "fine") should never be paid. To remove this lock screen, follow the instructions below.
| Name | NATIONAL SECURITY BUREAU malware |
| Threat Type | Ransomware, Crypto Virus, Files locker |
| Symptoms | Can't open files stored on your computer, previously functional files now have a different extension, for example my.docx.locked. A ransom demanding message is displayed on your desktop. Cyber criminals are asking to pay a ransom (usually in bitcoins) to unlock your files. |
| Distribution methods | Infected email attachments (macros), torrent websites, malicious ads. |
| Damage | All files are encrypted and cannot be opened without paying a ransom. Additional password stealing trojans and malware infections can be installed together with a ransomware infection. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar malware examples
In terms of current malware trends, NATIONAL SECURITY BUREAU is a rather unusual scam. In most cases, these scams are promoted by various malicious websites. Furthermore, most do not claim that user is breaking any laws.
They often state that the system is somehow damaged (e.g., infected, missing files, etc.) and users are encouraged to contact fake 'tech support' and pay for services (that are not even needed, since the system is safe) or download fake system repair tools (that promote in-app purchases or proliferate other malware).
The list of such scams includes System Support Alert, Microsoft Antivirus, The Gotham Font Was Not Found, Your Windows Computer is Infected With (4) Viruses!, and many others.
How did potentially unwanted programs install on my computer?
Screen-locking viruses are proliferated in various ways. The most popular distribution methods are potentially unwanted programs (PUPs), spam emails (malicious attachments), peer-to-peer (P2P) networks, third party software download sources, fake software updaters, and trojans.
Potentially unwanted programs proliferate malware by displaying intrusive advertisements that redirect to malicious websites and run scripts designed to download and install viruses. Infectious attachments typically come in the format of JavaScript files or MS Office documents.
As with intrusive advertisements, once opened, these files execute scripts that stealthily download/install malware. P2P networks (eMule, torrents, etc.) and various unofficial download sources (free file hosting websites, freeware download websites, and so on) present malicious executables as legitimate software.
In this way, users are tricked into downloading and installing malware. Fake updaters infect the system by abusing outdated software bugs/flaws or simply downloading and installing malware rather than updates. Trojans are probably the simplest ones - most open "backdoors" for other high-risk viruses to infiltrate the system.
How to avoid installation of potentially unwanted applications?
The main reasons for computer infections are poor knowledge and careless behavior. The key to safety is caution. For these reasons, pay close attention when browsing the Internet and downloading/installing software. Be sure that your selected software is legitimate and remember that it should be downloaded from official sources only, using direct download links.
Third party downloaders/installers often include ("bundle") PUPs, and thus these tools should never be used. Furthermore, never open email attachments that seem irrelevant or have been sent from suspicious/unrecognizable email addresses. In these cases, delete the emails immediately.
Keep installed software up-to-date and use a reputable anti-virus/anti-spyware suite. Remember that criminals proliferate malware via fake updaters. Therefore, you are advised to use implemented update functionality or tools provided by the official developer only.
Text presented in NATIONAL SECURITY BUREAU lock screen (Payment tab):
NATIONAL SECURITY BUREAU NSB
Your computer was automatically blocked. Reason: Pirated software found on this computer.
Your computer is now blocked. 02 files have been temporarily blocked on your computer.To regain computer access and restore you are required to pay a fine of 250 USB Blocked files will be permanently removed from your computer if the fine is not paid. The NSB has two ways to pay a fine:
1. You can pay your fine online through BitCoin. Bitcoin is available nationwide. Click the tabs below to find the nearest vendor. Your computer will be unlocked after you make your payment.
2. You can come to your provincial courthouse and pay your fine at the Cashiers window.
your computer will be unlocked within 4-5 working days.
To regain access transfer bitcoins to the following address (click to copy): 198tX7NmLg6o8qcTT2Uv9cSBVzN3oEozpv
After the payment is finalised enter Transfer ID below.
Amount 0.661 BTC
If the fine is not paid, a warrant will be issued for your arrest, which will be forwarded to your local authorities. You will be charged, fined, convicted for up to 5 years.
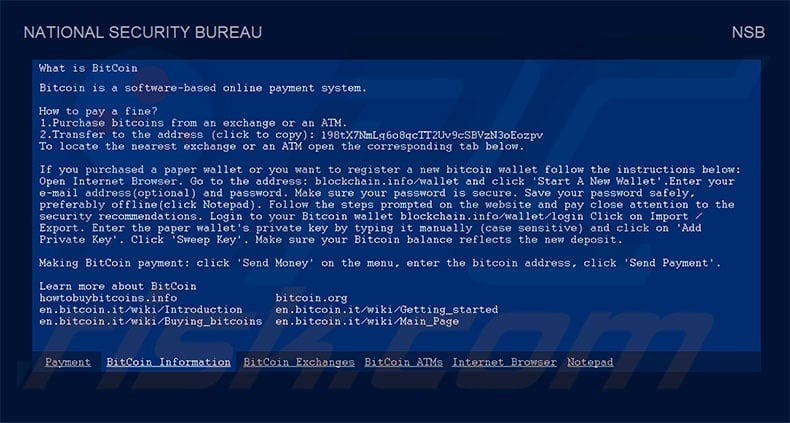
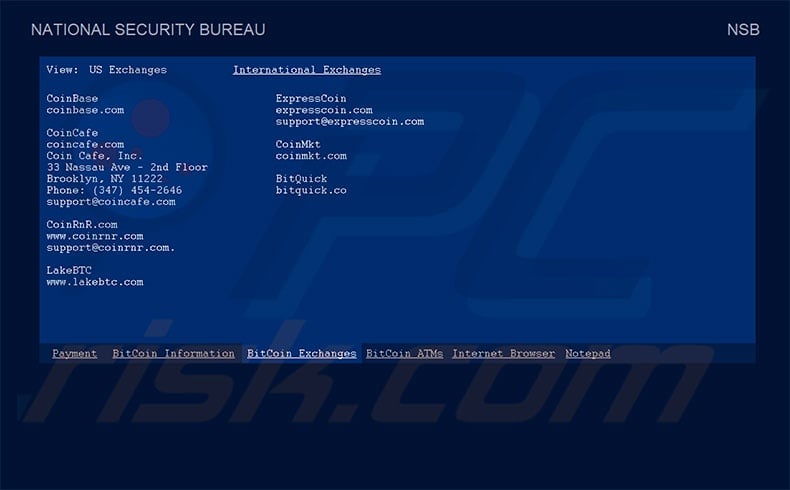
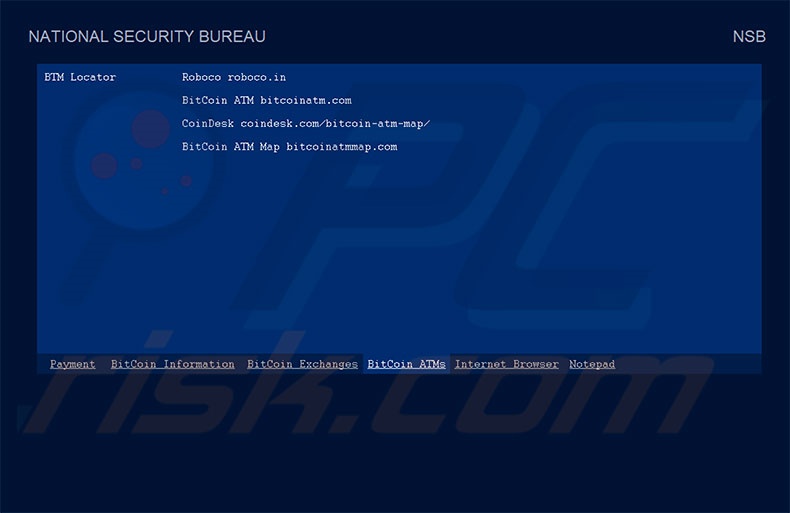
Other tabs of NATIONAL SECURITY BUREAU screen lock:
BitCoin Information:
BitCoin Exchanges:
BitCoin ATMs:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is "NATIONAL SECURITY BUREAU"?
- STEP 1. "NATIONAL SECURITY BUREAU" virus removal using safe mode with networking.
- STEP 2. "NATIONAL SECURITY BUREAU" virus removal using System Restore.
"NATIONAL SECURITY BUREAU" virus removal:
Step 1
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer starting process press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
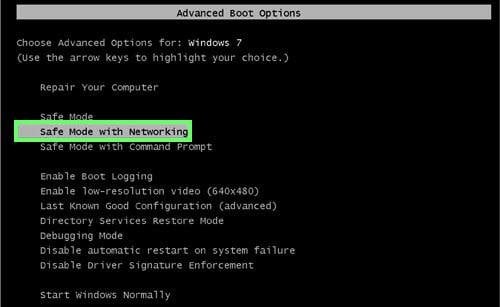
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Go to the Windows 8 Start Screen, type Advanced, in the search results select Settings. Click on Advanced Startup options, in the opened "General PC Settings" window select Advanced Startup. Click on the "Restart now" button. Your computer will now restart into "Advanced Startup options menu". Click on the "Troubleshoot" button, then click on "Advanced options" button. In the advanced option screen click on "Startup settings". Click on the "Restart" button. Your PC will restart into the Startup Settings screen. Press "5" to boot in Safe Mode with Networking Prompt.
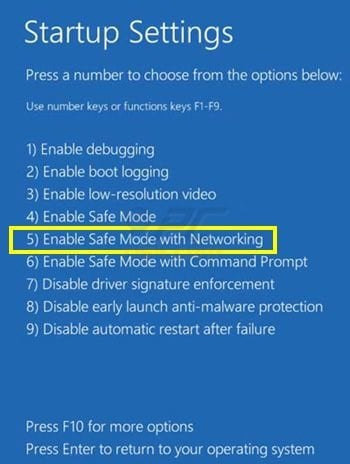
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options". In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
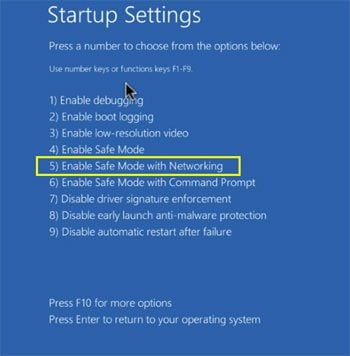
Video showing how to start Windows 10 in "Safe Mode with Networking":
Step 2
Log in to the account infected with the "NATIONAL SECURITY BUREAU" virus. Start your Internet browser and download a legitimate anti-spyware program. Update the anti-spyware software and start a full system scan. Remove all entries detected.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
If you cannot start your computer in Safe Mode with Networking, try performing a System Restore.
Video showing how to remove viruses using "Safe Mode with Command Prompt" and "System Restore":
1. During your computer starting process, press the F8 key on your keyboard multiple times until the Windows Advanced Options menu appears, and then select Safe Mode with Command Prompt from the list and press ENTER.
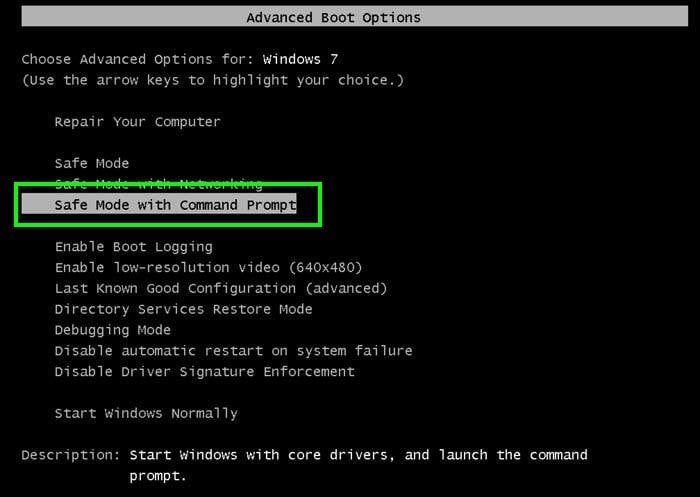
2. When Command Prompt Mode loads, enter the following line: cd restore and press ENTER.
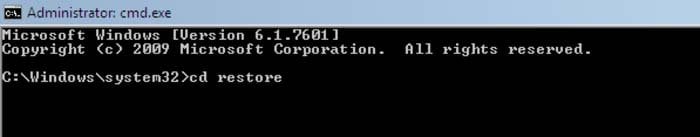
3. Next, type this line: rstrui.exe and press ENTER.
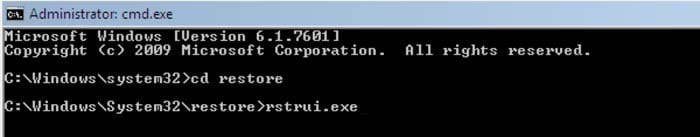
4. In the opened window, click "Next".
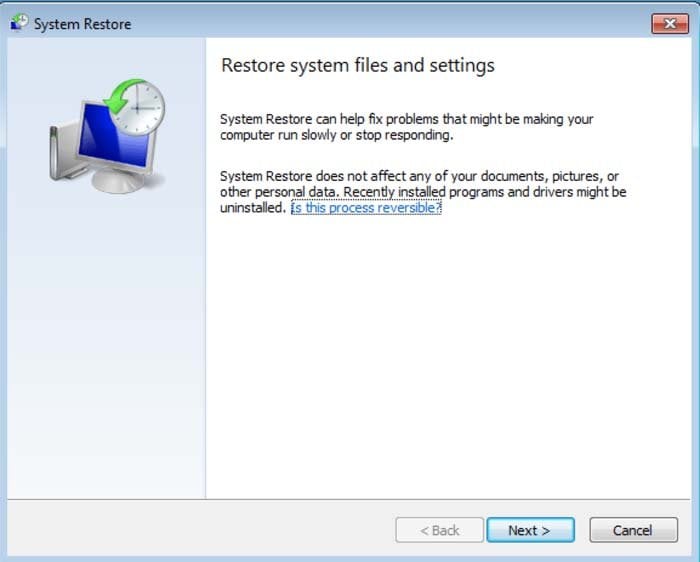
5. Select one of the available Restore Points and click "Next" (this will restore your computer system to an earlier time and date, prior to the "NATIONAL SECURITY BUREAU" virus infiltrating your PC).
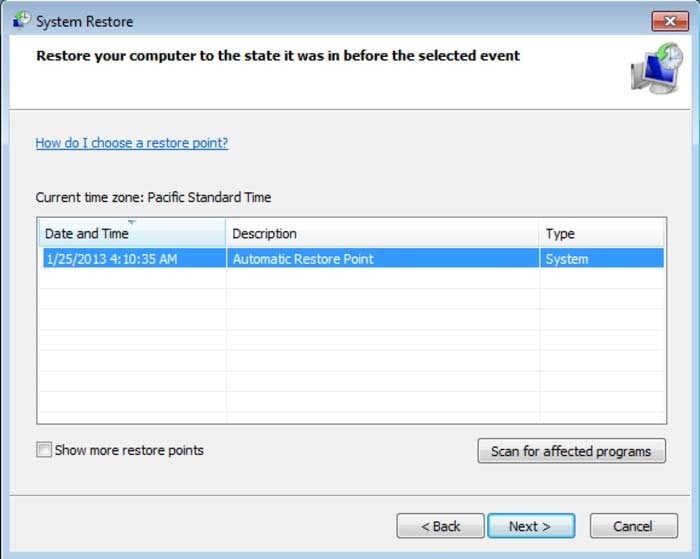
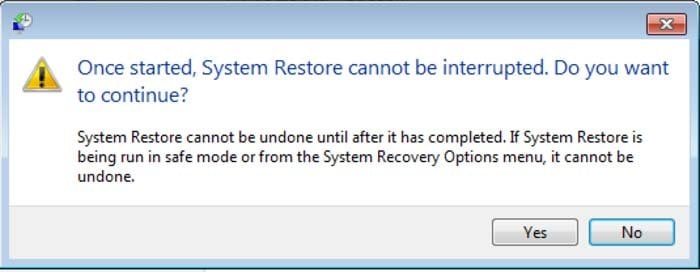
6. In the opened window, click "Yes".
7. After restoring your computer to a previous date, download and scan your PC with recommended malware removal software to eliminate any remnants of the "NATIONAL SECURITY BUREAU" virus.
If you cannot start your computer in Safe Mode with Networking (or with Command Prompt), boot your computer using a rescue disk. Some viruses disable Safe Mode making its removal complicated. For this step, you require access to another computer.
After removing the "NATIONAL SECURITY BUREAU" virus from your PC, restart the computer and scan it with legitimate anti-spyware software to remove any possible remnants of this security infection.
Other tools known to remove this scam:
Frequently Asked Questions (FAQ)
My computer is infected with NATIONAL SECURITY BUREAU malware, should I format my storage device to get rid of it?
No, NATIONAL SECURITY BUREAU malware can be removed without resorting to formatting.
What is the purpose of NATIONAL SECURITY BUREAU malware?
NATIONAL SECURITY BUREAU malware aims to trick victims into paying a fake fine (ransom) to unlock their devices. Hence, the end goal is to generate revenue at victims' expense.
How did NATIONAL SECURITY BUREAU malware infiltrate my computer?
Malware is primarily proliferated via drive-by downloads, spam emails/messages, online scams, malvertising, dubious download sources (e.g., unofficial and free file-hosting sites, P2P sharing networks, etc.), illegal software activation tools ("cracks"), and fake updates. Some malicious programs can even self-spread through local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
Should I pay the ransom?
We do not recommend paying the ransom. There are no guarantees that the cyber criminals will uphold their end of the bargain. Furthermore, by paying – victims unintentionally support this criminal activity.
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner is designed to detect and eliminate all manner of threats. It is capable of removing practically all known malware infections. Note that since high-end malicious software usually hides deep within systems – performing a full system scan is crucial.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion