How to avoid computer infections caused via DHL malspam campaign
Phishing/ScamAlso Known As: DHL spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is DHL Email Virus?
Similar to Offer Email Virus and many others, "DHL Email Virus" is a spam email campaign used to proliferate a high-risk trojan called LokiBot. Cyber criminals send thousands of emails by presenting them as notifications of deliveries. Users are encouraged to open attached documents. Once opened, however, these files infect the system with LokiBot.

More about this campaign
Cyber criminals send thousands of emails presenting them as notifications from DHL companies. The messages state that users have received packages, which have not yet been delivered.
To retrieve their deliveries, users must download and print the attached document, however, this is a scam - the opened attachment will immediately download and install LokiBot onto the system. DHL is a legitimate logistics company and has nothing to do with this spam campaign.
Cyber criminals often claim to be employees of legitimate companies or governmental institutions in attempts to give the impression of legitimacy. Users are much more likely to open files when they are received from familiar names. Once infiltrated, LokiBot starts recording user-system information.
Depending on the infiltrated operating system (Windows or Android), LokiBot's behavior may slightly differ, however, its main purpose remains identical: to gather information such as logins/passwords, web browsing activity, and so on.
The presence of this malware can lead to significant financial loss and serious privacy issues, since cyber criminals might gain access to accounts on social networks, banks, and so on.
If you have already opened a "DHL Email Virus" campaign attachment, there is a high probability that your system is infected with the LokiBot trojan. Therefore, scan it with a reputable anti-virus/anti-spyware suite and remove all detected threats.
| Name | DHL spam |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Symptoms | Trojans are designed to stealthily infiltrate victim's computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Examples of similar malware
There are dozens of trojans that share similarities with LokiBot. Adwind, TrickBot, and Emotet are just some examples from a long list.
As with LokiBot, most are designed to record data. In some cases, however, trojans proliferate other viruses (usually, ransomware) and mine cryptocurrencies. In summary, all trojan-type viruses pose a significant threat to your privacy and computer safety, and thus should be eliminated immediately.
How did DHL Email Virus infect my computer?
The "DHL Email Virus" campaign encourages users to download a dubious file. It is presented as a PDF office, however, but is an executable that downloads and installs LokiBot onto the system. As mentioned above, LokiBot targets only Windows and Android operating systems. Thus, users of other platforms are safe.
How to avoid installation of malware?
To prevent these infections, be cautious when browsing the Internet. Carefully analyze each email attachment received. If the file is irrelevant or has been received from an unrecognizable email address, do not open it. In addition, have a legitimate anti-virus/anti-spyware suite installed and running.
These tools can eliminate malicious files immediately after download. The main reasons for computer infections are poor knowledge and careless behavior, and the key to safety is caution. If you have already opened "DHL Email Virus" attachment, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "DHL Email Virus" email message:
Subject: Your Parcel has arrived
ORDER: PI#545223
ARRIVAL PERIOD: Yesterday
Dear Customer,
Your parcel has arrived at the post office. Our courier was unable to deliver the parcel to you.
Please click the attachment to DOWNLOAD AND PRINT RECIEPT
To receive your parcel, please go to the nearest office and show this receipt.
Best Regards, DHL Express Team.
Second sample of "DHL Email Virus" email message distributing either LokiBot or Agent Tesla (depending on the variant):

Text presented in this email:
DHL
AWB NO: 5563164600
ARRIVAL DATE:
Dear Cpnsignee,
Your parcel has arrived at the office. Our courier was unable to deliver the parcel to you due to wrong address from our customer.
To receive your parcel, please go to our closest office to show this AWB/invoice
please click the attachment to download and print invoice
Best regards,
The DHL Team.
Third sample of "DHL Email Virus" email message distributing LokiBot:

Text presented in this email:
Subject: Arrival Notice For BL – 08/23/2018 / Vessel – DHL Express
DHL EXPRESS INTERNATIONAL
The following Package Has been sent via DHL Express International,
Your parcel has been Delivered.
At the request of The Account Holder this notice
informs you that the status of the shipment Is Now Complete.
In order to ensure that your shipment is transferred as soon as possible through
our network, each package requires a single bill of lading.
The details that you have telephoned to our Customer Service team have already
been captured in this electronic bill of lading.
Please validate these details.
Click Here
LokiBot trojan process in Windows Task Manager :
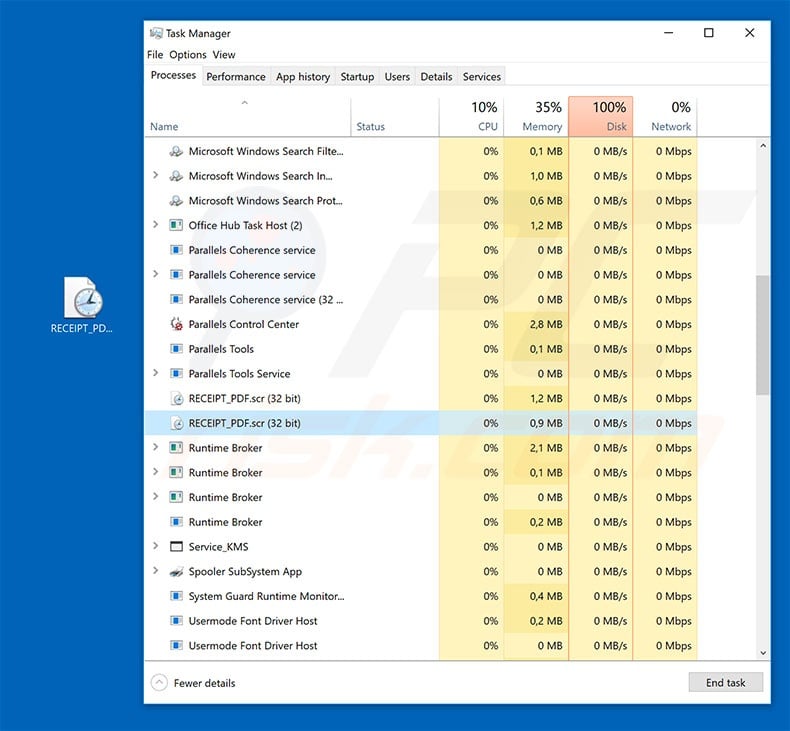
Another variant of "DHL Email Virus" email spam campaign (also proliferates LokiBot). The attachment is named "AWB Number 1428252044.iso" which contains an executable with the same name. The executable is LokiBot trojan.
Screenshot of email:

Text presented within this email:
Dear -
I have arrived with your consignment. But I am unable to reach you.
I cannot locate the final physical address on the airwaybill for this delivery.Please find your attached contact form. Also I attached the commercial invoice I received for this.
I attached my personal phone number too for easy contact.
Please check file and confirm the details.
I await your kind reply. Urgent.
Kind regards,
Dries Derwael
Senior Customer Retention AdvisorT: +3227155390
DHL Express | Woluwelaan 151 | 1831 Diegem
www.dhlexpress.be
Screenshot of LokiBot's process ("AWB Number 1428252044.exe") in Windows Task Manager:
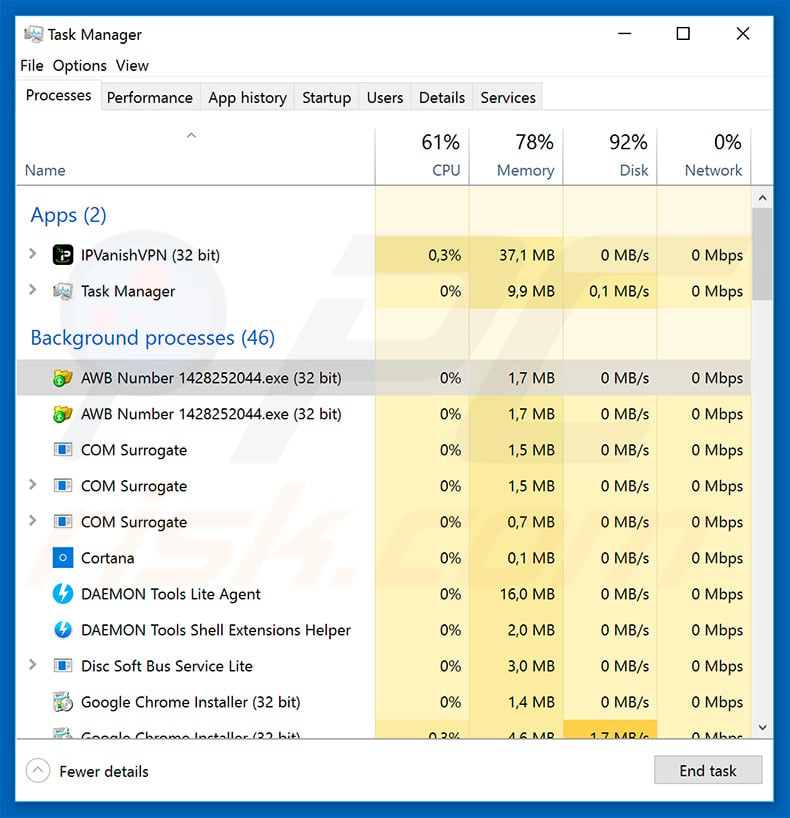
IMPORTANT NOTE! A variant of "DHL Email Virus" distributes a Remote Administration Tool (RAT) called Remcos. You can read more about this "DHL Email Virus" campaign variant in this article.
Screenshot of "DHL Email Virus" email message that distributes Remcos:
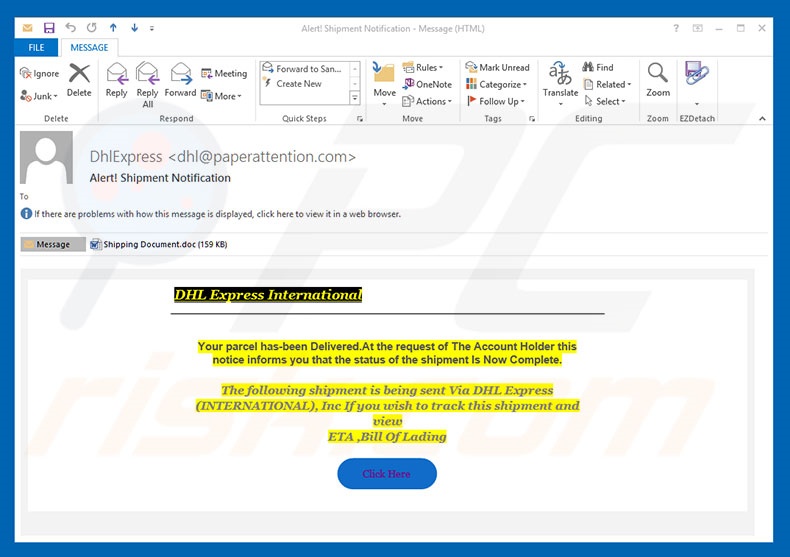
Text presented within this email:
Subject: Alert! Shipment Notification
DHL Express International
Your parcel has-been Delivered.At the request of The Account Holder this notice informs you that the status of the shipment Is Now Complete.
The following shipment is being sent Via DHL Express (INTERNATIONAL), Inc If you wish to track this shipment and view
ETA ,Bill Of Lading
Screenshot of malicious attachment distributed using this campaign:
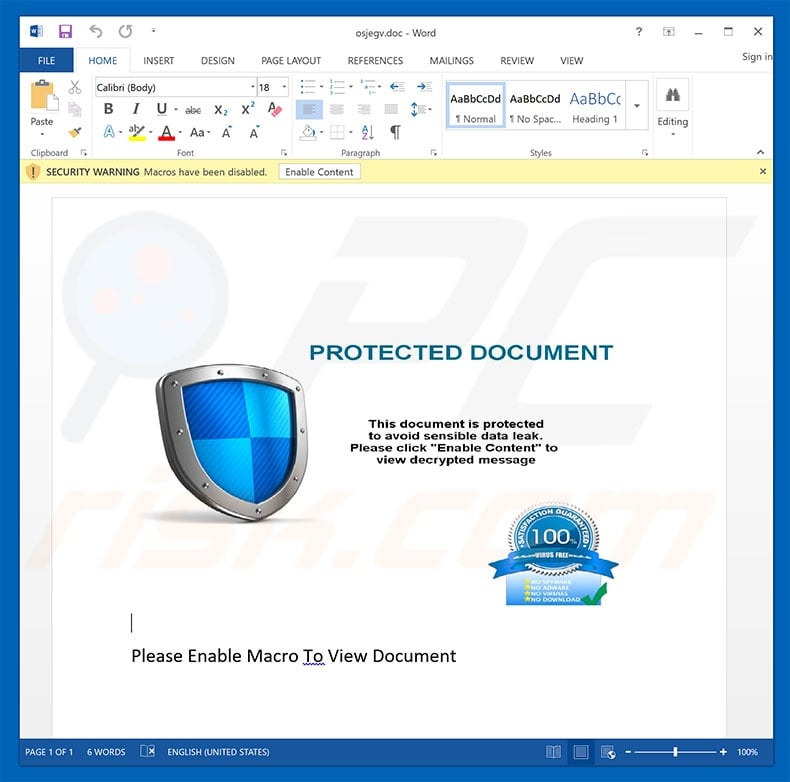
Another variant of "DHL Email Virus" email spam campaign (distributes Remcos RAT):
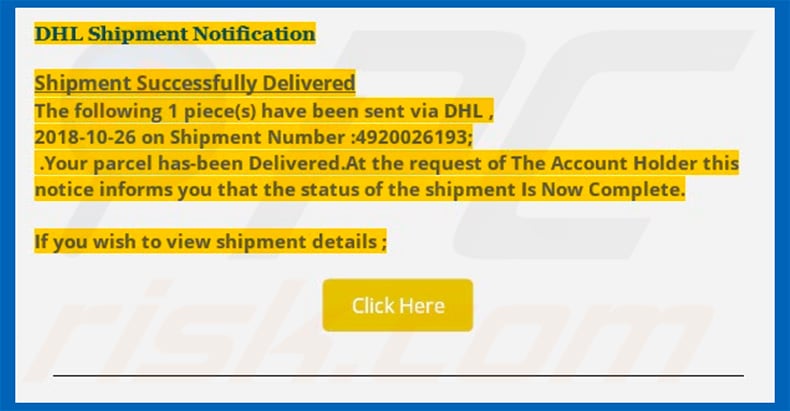
Text presented within this email:
Subject: DHL Shipping of Original invoice B/L dated 26/10/2018
DHL Shipment Notification
Shipment Successfully Delivered
The following 1 piece(s) have been sent via DHL ,
2018-10-26 on Shipment Number :4920026193;
Your parcel has-been Delivered.At the request of The Account Holder this notice informs you that the status of the shipment Is Now Complete.
If you wish to view shipment details ;
Screenshot of malicious document attached to this email:
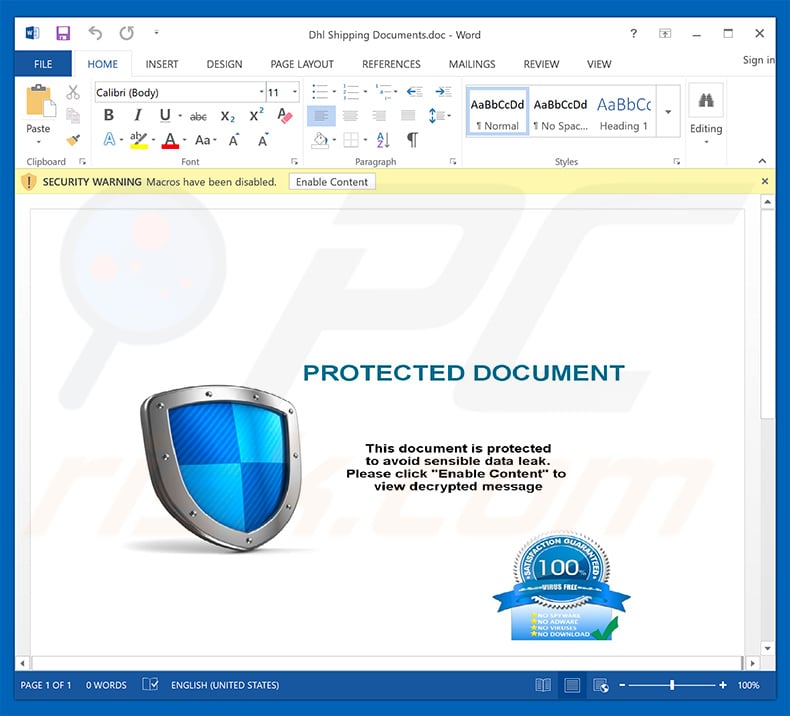
IMPORTANT NOTE! This spam campaign is also used to proliferate another trojan called FormBook. The attachment usually comes in MS Word (.doc or .docx) format. In our examined example the attachment was named "Correction Form.doc".
Screenshot of the email:

Text presented within this email:
Dear Customer,
Your packages arrived at our post service since 21st January, 2019.
Our dispatch agent was unable to deliver the packages to you due to incorrect delivery address details on the package registry as recorded by the sender.
Please kindly check the attached details form and make correction to your delivery address to enable us reschedule your package deliveryBest Regards.
Thanks for choosing Dhl Express.
Warm Regards,
DHL EXPRESS......
CONFIDENTIALITY CAUTION: This message is intended only for the use of the individual or entity to whom it is addressed and may be confidential in nature. If you are not the intended recipient, please notify us immediately by return e-mail and please do delete this message. You should not disseminate, distribute, copy or disclose any information contained herein to any third party. **Please consider the environment before printing this email**
Another malicious attachment (which injects GandCrab 5.2 ransomware) distributed using "DHL Email Virus" spam campaign:
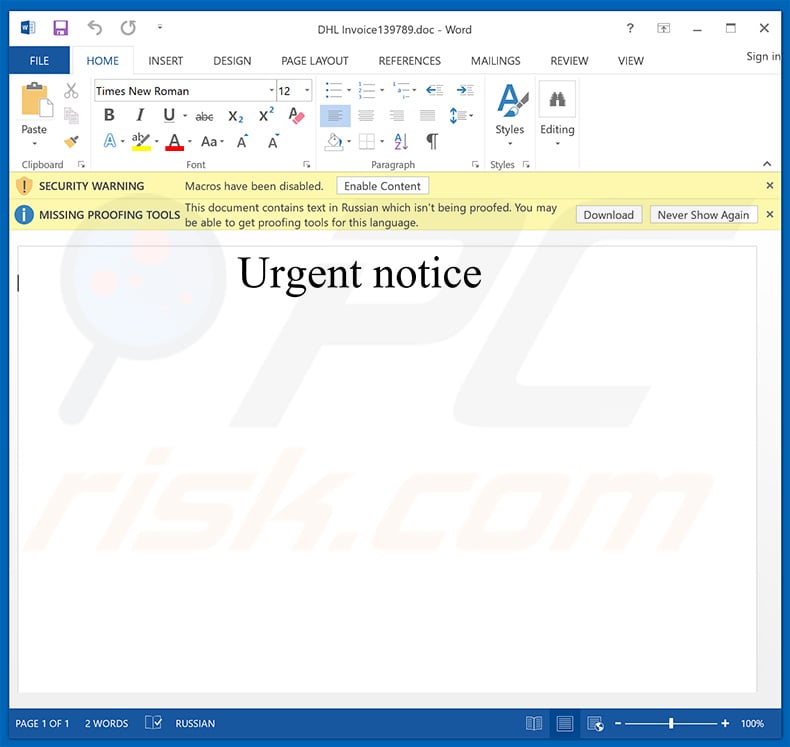
Update December 13, 2019 - Crooks have released yet another variant of DHL spam cmapaign, which now delivers a completely different attachment - an HTML file which asks to enter email credentials. Once entered, this information is saved in a remote server controlled by cyber criminals.
After gaining access to victim's email, crooks can cause a lot of damage, since a lot of people use the same password for multiple accounts. In addition, hijacked emails can be used to steal other accounts by abusing the password recovery feature.
Screenshot of this spam email:
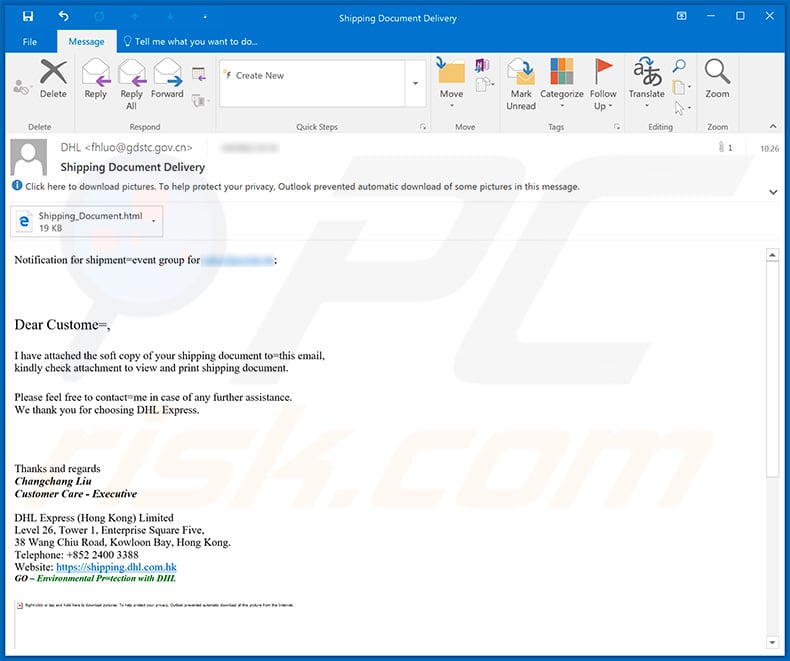
Text presented within:
Subject: Shipping Document Delivery
Notification for shipment=event group for ********;
Dear Custome=,
I have attached the soft copy of your shipping document to=this email,
kindly check attachment to view and print shipping document.
Please feel free to contact=me in case of any further assistance.
We thank you for choosing DHL Express.
Thanks and regards
Changchang Liu
Customer Care - Executive
DHL Express (Hong Kong) Limited
Level 26, Tower 1, Enterprise Square Five,
38 Wang Chiu Road, Kowloon Bay, Hong Kong.
Telephone: +852 2400 3388
Website: hxxps://shipping.dhl.com.hk
GO – Environmental Pr=tection with DHL
CONFIDENTIALITY NOTICE: Thi= message is from DHL and may contain confidential business information.
It is intended solely for the use of the individual to whom it is addressed=2E If you are not the intended recipient
please contact the sender and delete this message and any attachment from y=ur system. Unauthorized publication,
use, dissemination, forwarding, printing or copying of this E-Mail and its =ttachments is strictly prohibited.
Screenshot of the malicious HTML attachment ("Shipping_Document.html"):
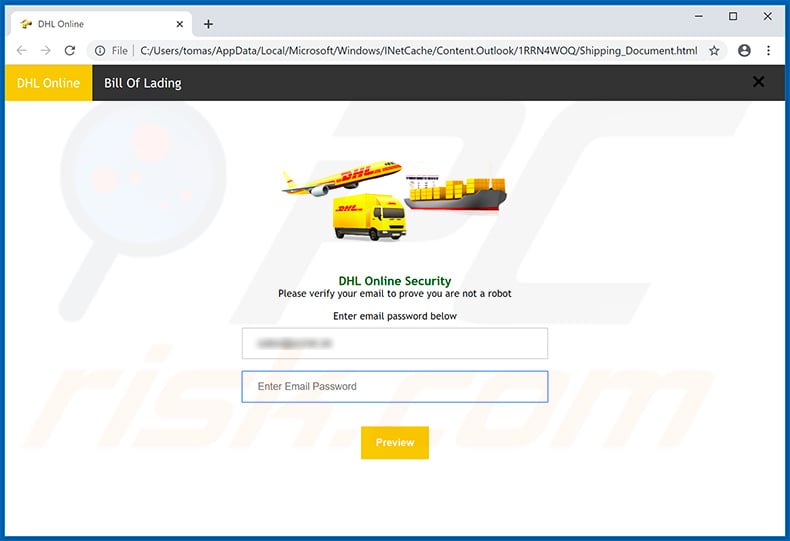
Text presented within:
DHL Online Bill Of Lading
DHL Online Security
Please verify your email to prove you are not a robotEnter email password below
-Enter Email Password
Preview
Another variant of "DHL" spam campaign used for phishing purposes:
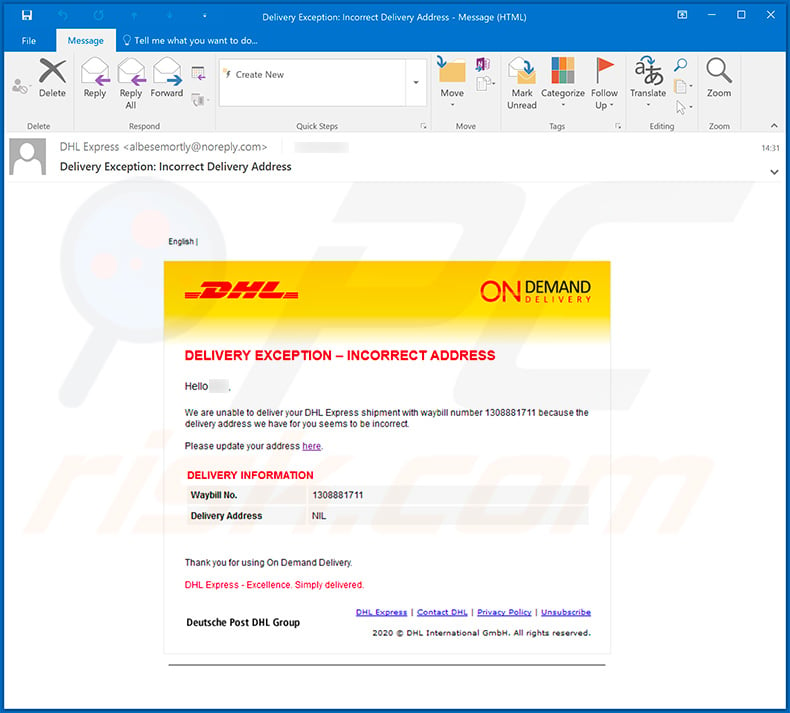
Text presented within this email:
Subject: Delivery Exception: Incorrect Delivery Address
DELIVERY EXVEPTION - INCORRECT ADDRESS
Hello ****,
We are unable to deliver your DHL Express shipment with waybill number 1308881711 because the delivery address we have for you seems to be incorrect.
Please update your address here.
DELIVERY INFORMATION
Waybill No. 1308881711
Delivery Address NILThank you for using On Demand Delivery
DHL Express - Excellence. Simply delivered.
Deutsche Post DHL Group
DHL Express | Contact DHL | Privacy Policy | Unsubscribe
2020 © DHL International GmbH. All rights reserved.
Screenshot of a phishing website promoted via this email:

Yet another variant of DHL spam campaign distributing a malicious attachment:
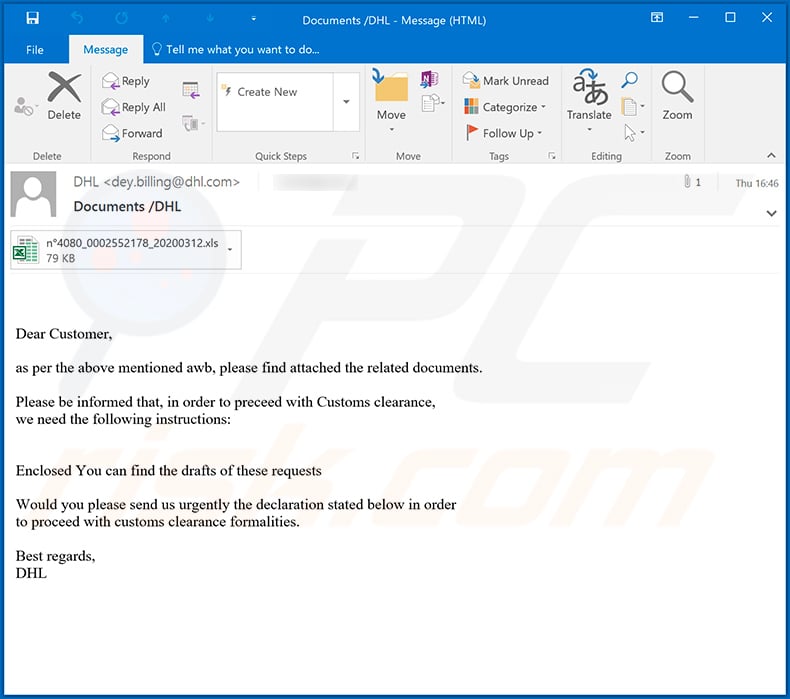
Text presented within this email:
Subject: Documents /DHL
Dear Customer,
as per the above mentioned awb, please find attached the related documents.
Please be informed that, in order to preceed with Customs clearance,
we need the following instructions:
Enclosed You can find the drafts of these requestsWould you please send us urgently the declaration stated below in order
to proceed with customs clearance formalities.Best regards,
DHL
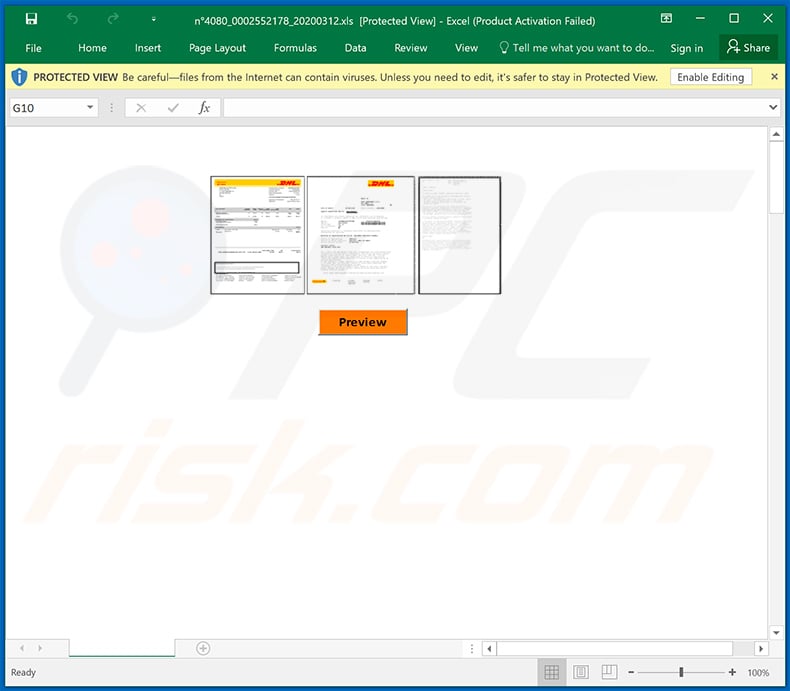
Screenshot of the malicious attachment (MS Excel file):
Yet another DHL spam email which distributes Agent Tesla RAT (the attachment is "DHL COURIER PICKUP CONFIRMATION.pdf.ace"):

Text presented within this email:
Subject: DHL Delivery Shipment COVID-19 Be Safe and Stay Strong.
Dear Valued Customer,
In the face of the challenges posed by the current global COVID-19 situation, DHL
Express maintains its service while protecting our employees and customers to the best of
our abilities.Please download your posted original documents attached to confirm accordingly if your
delivery details is correct, before we submit to our outlet office for dispatch to your door
step.Thank you for using DHL
Sincerely,
DHL ExpressThis is an auto-generated message sent to:Our Valued Customer.
Yet another DHL-related email distributing a malicious MS Word document ("INV, Shipping documents and BL draft.doc"):
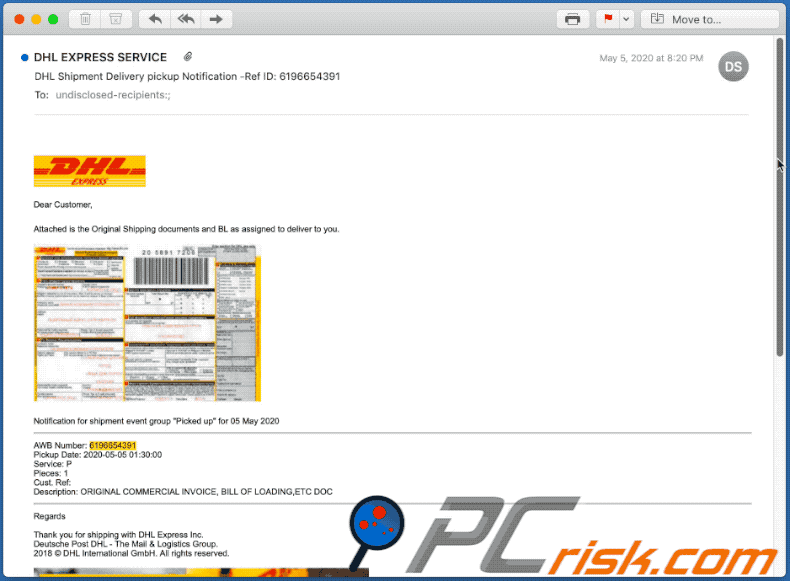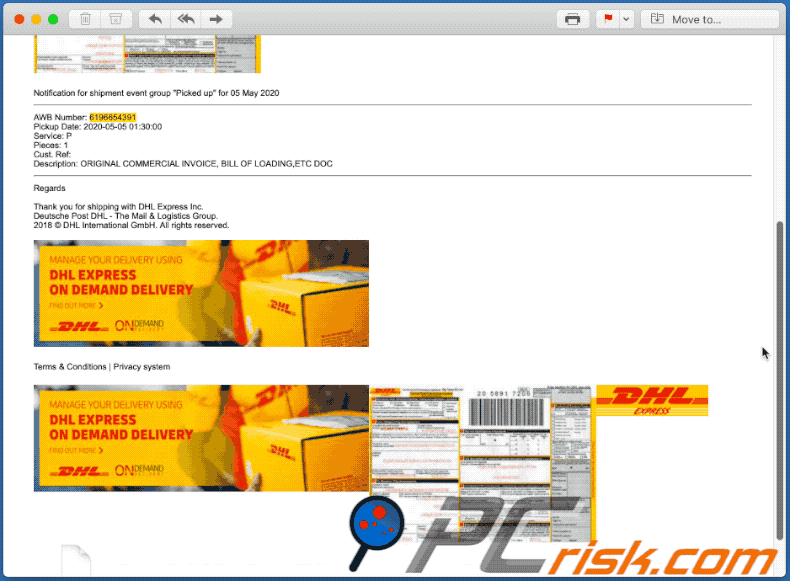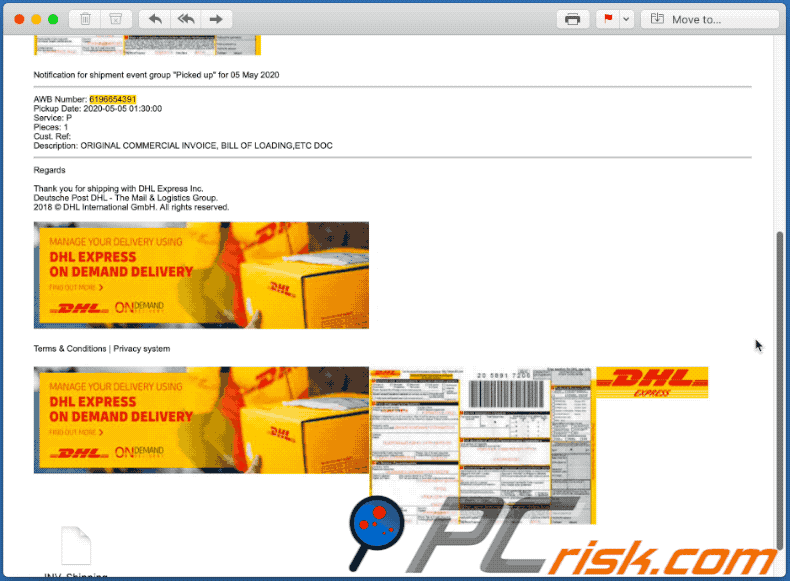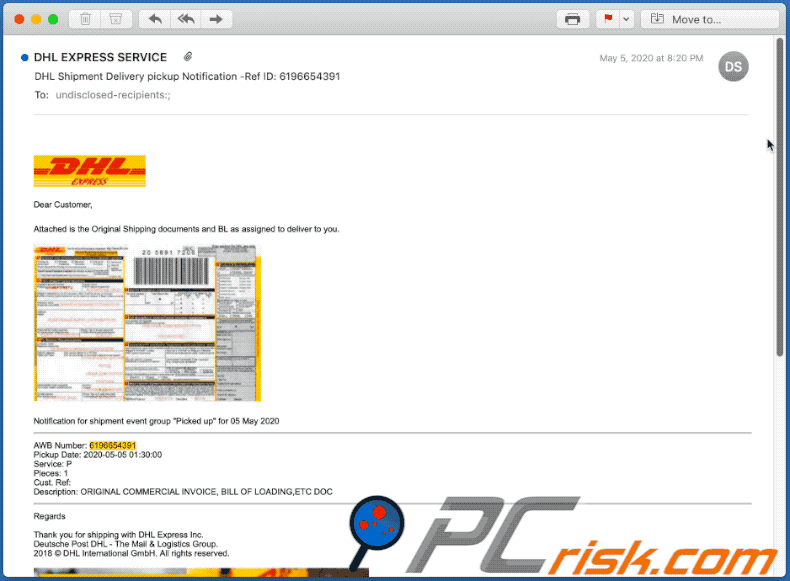
Text presented within:
Subject: DHL Shipment Delivery pickup Notification -Ref ID: 6196654391
Dear Customer,
Attached is the Original Shipping documents and BL as assigned to deliver to you.
Notification for shipment event group "Picked up" for 05 May 2020
AWB Number: 6196654391
Pickup Date: 2020-05-05 01:30:00
Service: P
Pieces: 1
Cust. Ref:
Description: ORIGINAL COMMERCIAL INVOICE, BILL OF LOADING,ETC DOC
Regards
Thank you for shipping with DHL Express Inc.
Deutsche Post DHL - The Mail & Logistics Group.
2018 © DHL International GmbH. All rights reserved.
Terms & Conditions | Privacy system
Example of yet another DHL-themed spam email which is designed to spread TrickBot trojan (the attachment is a .rar archive containing a malicious executable):
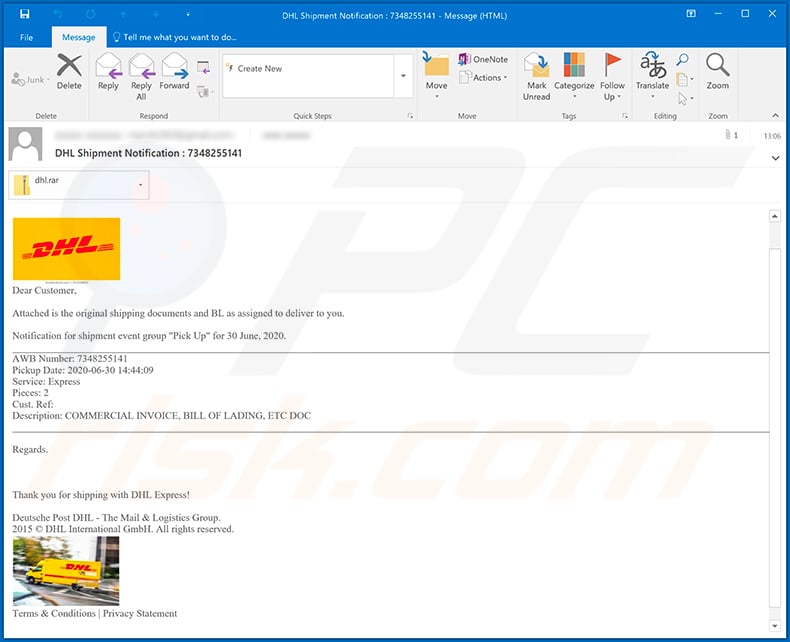
Text presented within:
Subject: DHL Shipment Notification : 7348255141
Dear Customer,
Attached is the original shipping documents and BL as assigned to deliver to you.
Notification for shipment event group "Pick Up" for 30 June, 2020.
AWB Number: 7348255141
Pickup Date: 2020-06-30 14:44:09
Service: Express
Pieces: 2
Cust. Ref:
Description: COMMERCIAL INVOICE, BILL OF LADING, ETC DOCRegards.
Thank you for shipping with DHL Express!
Deutsche Post DHL - The Mail & Logistics Group.
2015 © DHL International GmbH. All rights reserved.Terms & Conditions | Privacy Statement
Screenshot of yet another DHL-themed spam email used for phishing purposes:

Text presented within:
Subject: DHL DELIVERY RE-COMFIRMATION
On Demand Delivery
Dear Customer,Kindly re-confirm your address so that we can deliver the package on time.
Click Here to edit your delivery address and complete this shipment.
Note: If the above input is not correct, the shipment will be cancelled
Reception date: 07/07/2020
Logistics Team
Screenshot of a phishing website (fake DHL site) promoted via this email:

Another variant of a DHL-themed spam email used to promote a phishing website:
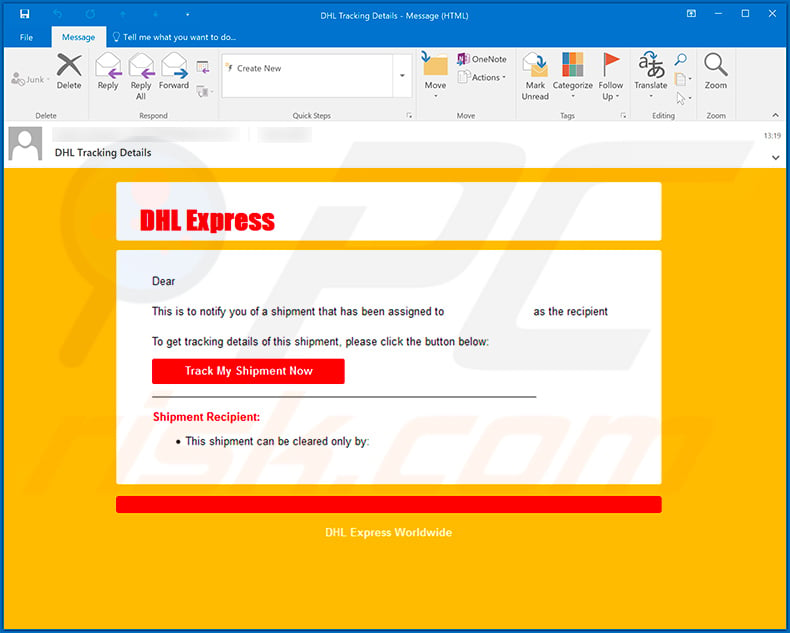
Text presented within:
Subject: DHL Tracking Details
DHL Express
Dear
This is to notify you of a shipment that has been assigned to as the recipient
To get tracking details of this shipment, please click the button below:
Track My Shipment Now
Shipment Recipient:
This shipment can be cleared only by:
DHL Express Worldwide
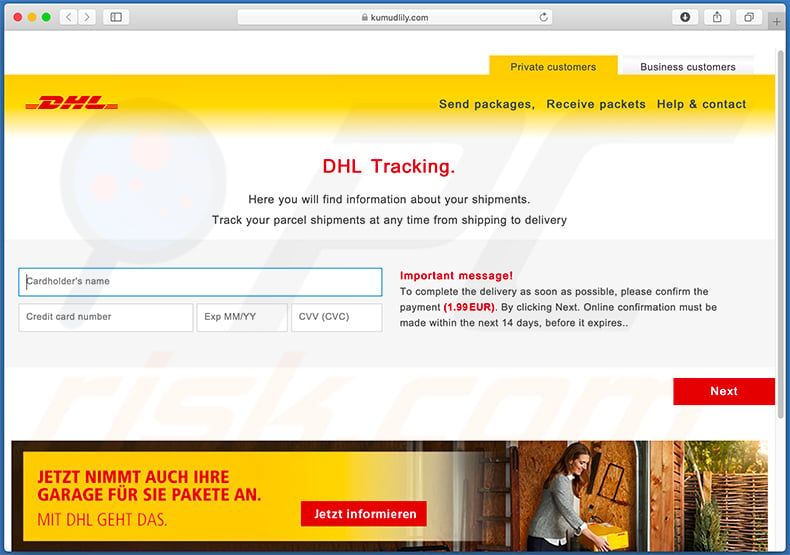
Screenshot of the promoted phishing site:

Example of yet another DHL-themed spam email (targeting German users) used to promote a phishing website:

Text presented within:
Subject: Your package is waiting for delivery.
Dhl Logo Black And White, HD Png Download - kindpng
Ihr Paket wartet auf die Lieferung.
Wichtige Benachrichtigung :
Um die Lieferung so schnell wie möglich abzuschließen, bestätigen Sie bitte die Zahlung (1.99 EUR)
Die Online-Bestätigung muss innerhalb der nächsten 7 Tage vor Ablauf erfolgen.
Folgen Sie meinen Paketen
Sie haben diese E-Mail erhalten, weil Sie bei DHL registriert sind.
2020 DHL Express.
Screenshot of the promoted phishing site:
Yet another DHL-themed spam email used to spread Agent Tesla RAT:
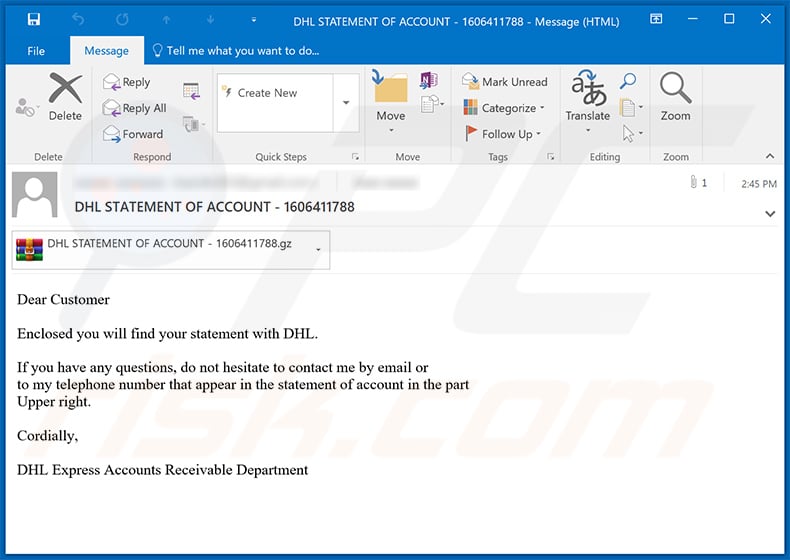
Text presented within:
Subject: DHL STATEMENT OF ACCOUNT - 1606411788
Dear Customer
Enclosed you will find your statement with DHL.
If you have any questions, do not hesitate to contact me by email or
to my telephone number that appear in the statement of account in the part
Upper right.Cordially,
DHL Express Accounts Receivable Department
Yet another example of DHL spam email used to spread Agent Tesla malware:

Text presented within:
Subject: AWB Number: 6278216733
Dear Customer,
Attached copies of agreement documents as assigned to deliver to you.
Notification for shipment event group "Pick Up" for 22nd April, 2021.AWB Number: 6278216733
Pickup Date: 2021-04-22 14:44:09
Service: Express
Pieces: 2
Cust . Ref:
Description: Agreement Docs & etcRegards
Thank you for shipping with DHL Express!DHL Express – Excellence. Simply delivered
Deutsche Post DHL Group- The Mail & Logistics Group.GOGREEN – Environmental protection with DHL
Please consider your environmental responsibility before printing this email.
A Lithuanian variant of DHL-themed spam email used to spread malware:

Text presented within:
Subject: DHL PRANEŠIMAS
Gerbiamas kliente,
Atkreipkite dėmesį, kad siuntėjas MMCITÉ PL SP. Z O.O. per „DHL Parcel"
išsiuntė siuntinį numeriu 23788390235.
Pristatymo adresas: J.Tumo-Vaizganto g. 9/1-63a LT-01108 - Vilnius -Lithuania .
Numatoma pristatymo data: kita darbo diena
patikrinkite sąskaitą faktūrą ir pristatymo duomenis pridedamame dokumente.
Suplanuoti pristatymo terminai bus nurodyti pranešime, kai kurjeris gaus paketą pristatymui.
Jūs nežinote, ar būsite nurodytu adresu? Dabar galite nuspręsti, kur jūsų siuntinys bus pristatytas.
Nukreipkite siuntinį į ir patogiai surinkite jį viename iš daugiau nei 10 000 DHL POP siuntų aptarnavimo punktų.
Patikrinkite, ar jūsų vietovėje nėra naujų POP.
Daugiau nei 80% taškų veikia iki 22.00 val. Ar ilgiau.
Mūsų tinklą sudaro Żabka, Inmedio, Relay, 1 minutė, abc, Kaufland, Shell stotys ir atskiri taškai mažesniuose miestuose.Nepavykus bandymo pristatyti kurjerį, išsiųsime paketą atsiimti DHL POP jūsų vietovėje.
Daugiau informacijos apie siuntos būseną svetainėje: DHL sekimas
Pagarbiai/Best regards,Karolis Pašiušis
Transporto vadybininkas/Freight forwarder
DHL Freight c/o DHL Logistics Lietuva UAB
Tel. +370 5 2361874
Mob. +370 656 96 013
karolis.pasiusis@dhl.comdirbu iš namų/working from home
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is DHL spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
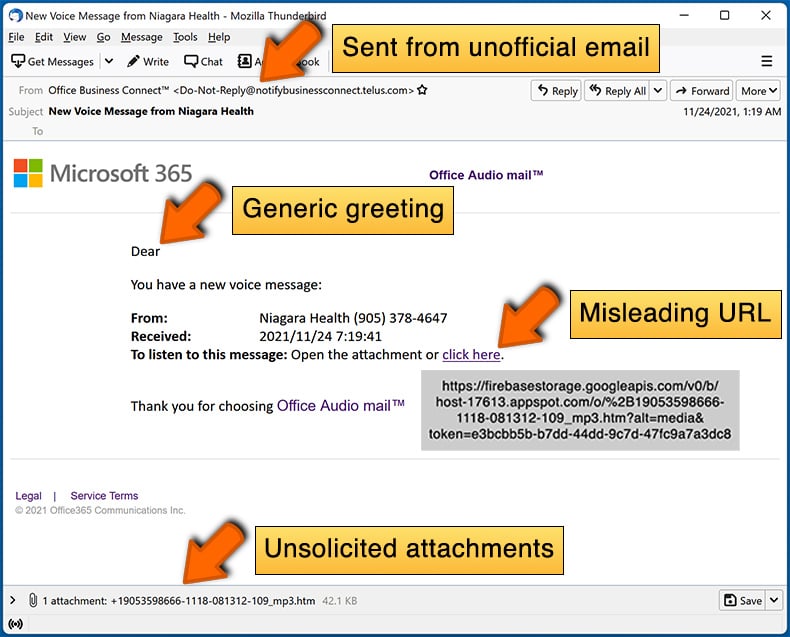
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
There is a high chance that your email has been leaked during a data breach and threat actors use it to deliver malware. This email is not personal. Cybercriminals sent it to all addresses they have in their database.
I have downloaded and opened a file attached to this email, is my computer infected?
It depends on the file type. If that file is executable, your computer is likely to be already infected. Microsoft Office documents, archive files, ISO files, and other files do not infect computers until additional steps are performed (e.g., macros commands in MS Office documents are enabled).
I have read the email but didn't open the attachment, is my computer infected?
No, it is safe to open emails without clicking links or opening attachments.
Will Combo Cleaner remove malware infections that were present in email attachment?
Yes, Combo Cleaner will remove malware from the operating system. It can detect almost all known malware. It is worth mentioning that computers infected with high-end malware have to be scanned using a full scan. Otherwise, high-end malware may remain undetected.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion