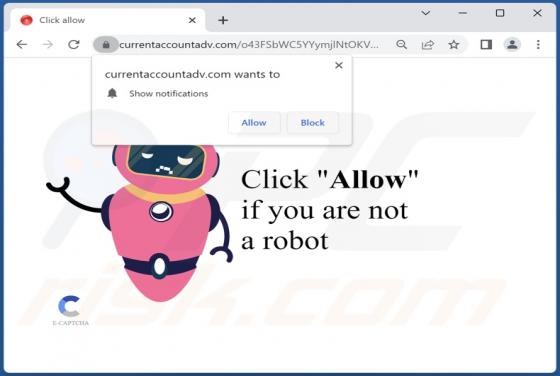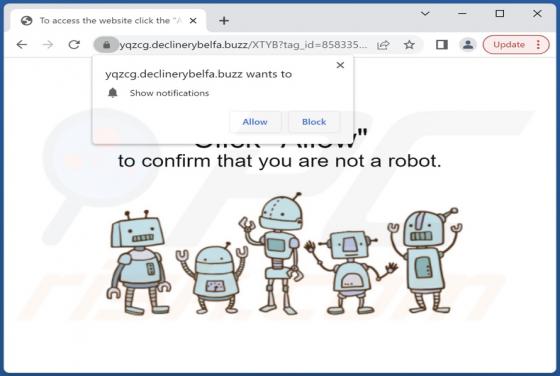
Declinerybelfa.buzz Ads
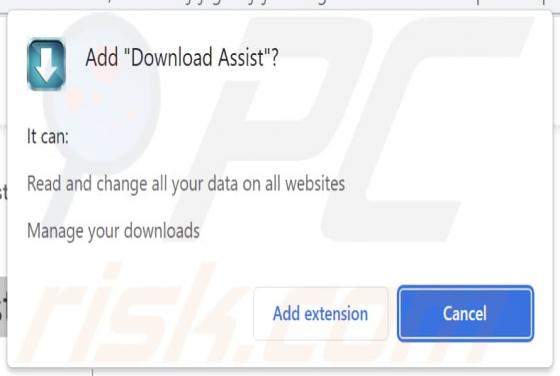
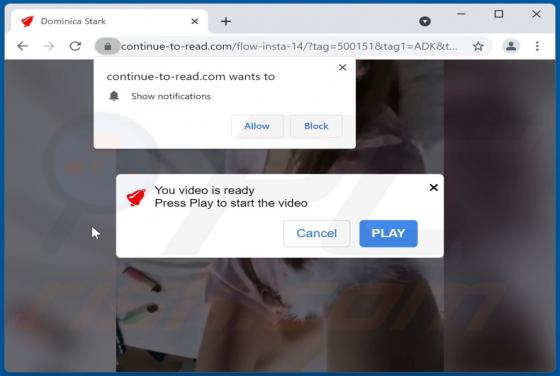
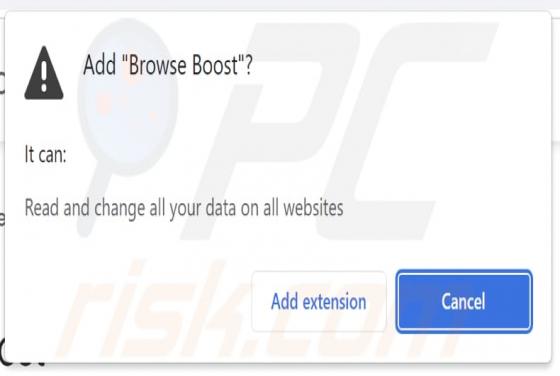
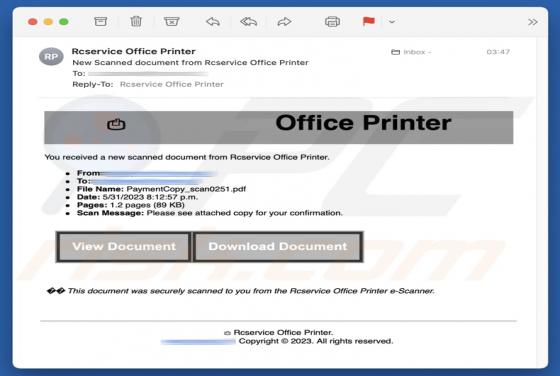
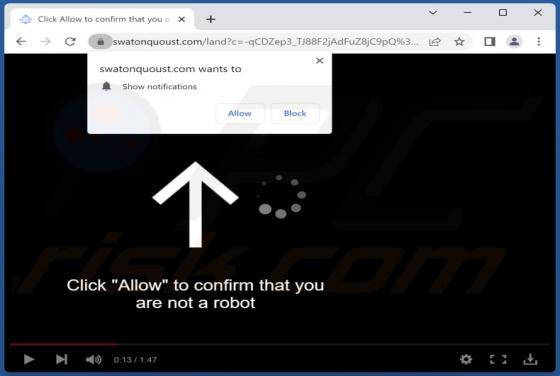
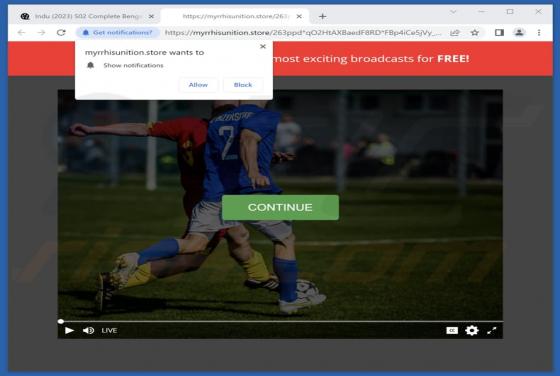
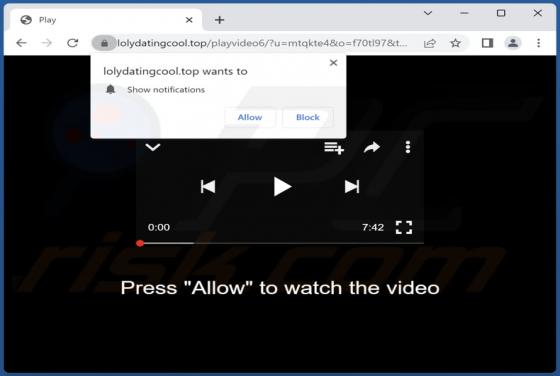
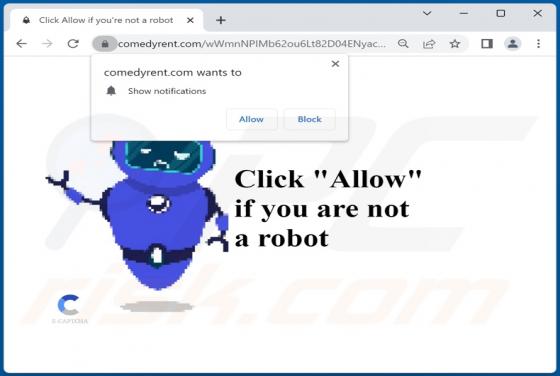
Declinerybelfa[.]buzz is a rogue page that aims to deceive visitors into enabling its browser notification delivery. Additionally, this webpage can generate redirects to other (likely untrustworthy/hazardous) sites. Most visitors to declinerybelfa[.]buzz and pages akin to it – access them via red