How to stop clipboard from pasting 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ
TrojanAlso Known As: 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ clipboard hijacker
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ?
89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ is the name of a malicious program. After analyzing it, we determined that this malware operates as a clipboard hijacker.
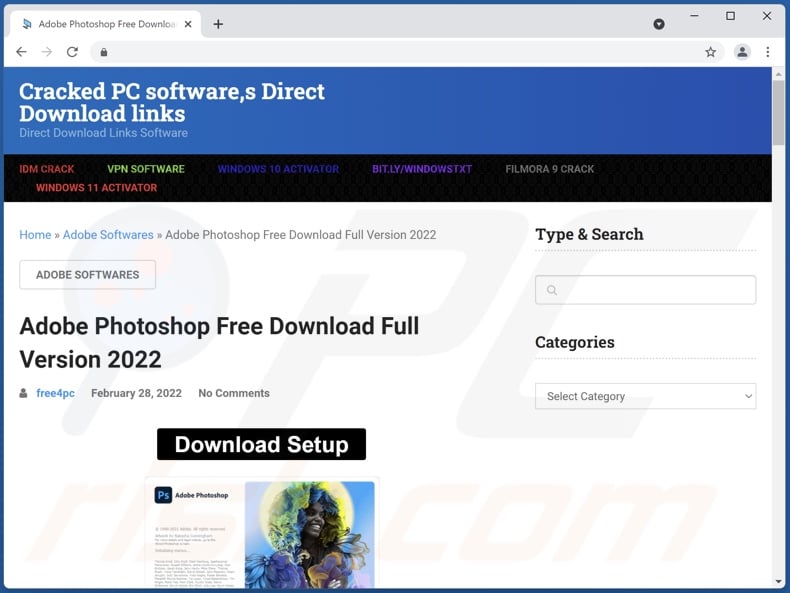
We discovered this program while inspecting websites offering "cracked" software. It is noteworthy that the installation setup that contained this clipboard hijacker was bundled with other unwanted software (e.g., fake Google Translate). Installers of this kind are often packed with adware, browser hijackers, and various PUAs.
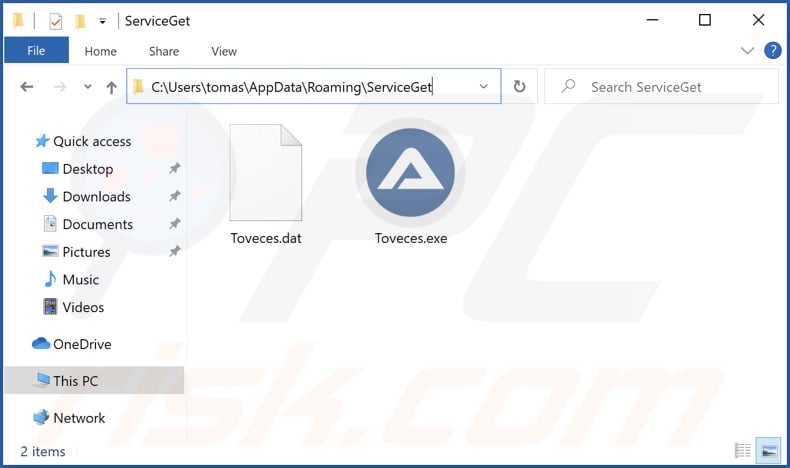
89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware overview
After being installed onto our test machine, this malicious program changed the clipboard data so that the output would be "89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ". In other words, when something was copied into the clipboard (copy-paste buffer), instead of the intended information - this character string was pasted.
It is evident that this program was supposed to operate as a proper clipper-type malware. The sting it pastes is a cryptocurrency wallet address. The difference between this hijacker and a fully-developed clipper is that the latter detects when a victim is making an outgoing cryptocurrency transaction - and only then changes the wallet's address copied into the clipboard with one in possession of the cyber criminals.
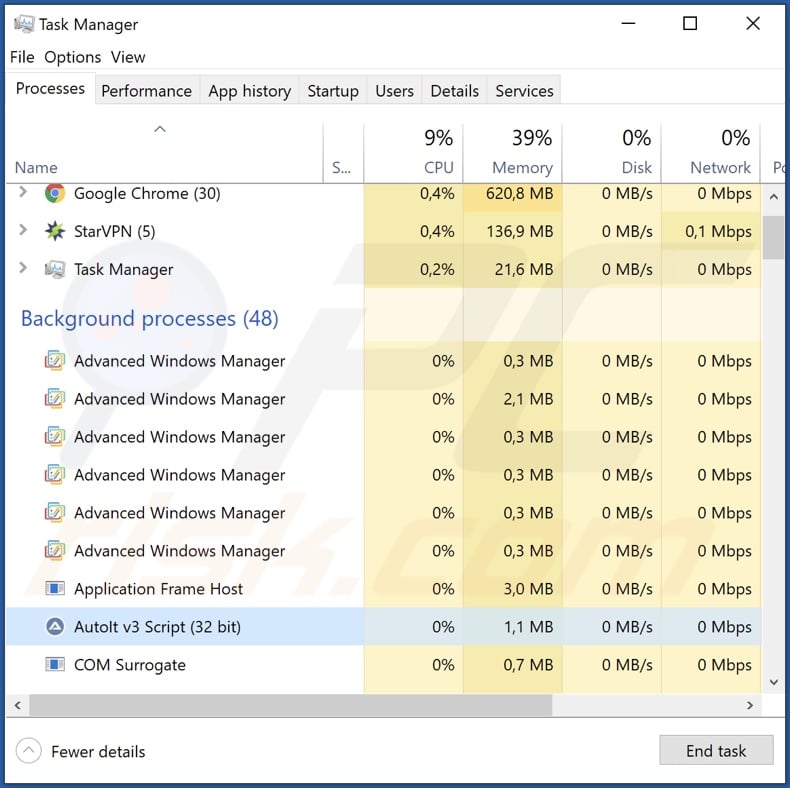
This disruptive copy/paste phenomenon can be stopped by ending the malware's process - AutoIt v3 Script (32 bit) - on Windows Task Manager. However, killing the process will not remove the program itself. Therefore, we strongly advise using an anti-virus to eliminate the malware in its entirely and get rid of the issue permanently.
As mentioned in the introduction, we noted that this clipboard hijacker's installer also contained other untrustworthy/harmful software. Hence, it is possible that if "89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ" is pasted on your system, other threats might be present as well. These programs may display intrusive and annoying advertisements, cause redirects or otherwise modify the browser, collect private data, and so on.
Therefore, users may experience system infections, serious privacy issues, financial losses, and even identity theft. We highly recommend running a complete system scan and removing all detected threats.
| Name | 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ clipboard hijacker |
| Threat Type | Trojan, Malware, Clipper, Clipboard Hijacker. |
| Detection Names | SecureAge APEX (Malicious), SentinelOne (Static ML) (Static AI - Suspicious PE), Webroot (Riskware.Gen), Full List Of Detections (VirusTotal) |
| Detection Names (malicious installer) | Avast (Win32:Malware-gen), Combo Cleaner (Dropped:Trojan.GenericKD.39163952), ESET-NOD32 (Multiple Detections), Kaspersky (Trojan-Downloader.Win32.Agent.xxzxqt), Microsoft (Trojan:Win32/Tnega!ml), Full List Of Detections (VirusTotal) |
| Malicious Process Name(s) | AutoIt v3 Script (32 bit) |
| Symptoms | When information is copied into the clipboard - it is not pasted, instead "89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ" is pasted. |
| Distribution Methods | 'Cracked' software websites, infected email attachments, malicious online advertisements, social engineering. |
| Damage | Decreased computer performance, privacy issues, possible additional malware infections. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Clipper malware examples
We have analyzed dozens of malicious programs that hijack and modify clipboard output. E-Clipper, Allcome, Frost, and Extended Clipper are a few examples of clippers. However, malware can have different abilities that can be in varied combinations. Therefore, there are many malicious programs that have clipper-type functionalities amidst other features, e.g., PENTAGON, Jester, S-400, and many others.
How did 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ install on my computer?
We downloaded the installation setup bundled with the 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ clipboard hijacker from a "cracked" software download website. Sites of this kind are commonly used in malware distribution; however, many dubious techniques are employed to spread malicious software.
The most popular proliferation methods include: drive-by (stealthy and deceptive) downloads, malicious attachments/links in spam emails and messages, untrustworthy download sources (e.g., Peer-to-Peer sharing networks and "cracked" software, freeware, and third-party download sites, etc.), online scams, and fake updates.
Malware is often disguised as or bundled with ordinary software/media. Infectious files can be in various formats, e.g., executables (.exe, .run, etc.), archives (ZIP, RAR, etc.), PDF and Microsoft Office documents, JavaScript, and so on. Once a malicious file is opened - the infection chain is triggered.
How to avoid installation of malware?
We highly recommend downloading only from official and verified channels. Additionally, programs must be activated and updated using functions/tools provided by legitimate developers, as those obtained from third-parties (e.g., illegal activation tools ["cracks"], unofficial updates, etc.) may cause system infections.
We advise against opening the attachments and links present in suspicious/irrelevant emails and messages, as they can contain malware.
It is paramount to have a reputable anti-virus installed and kept up-to-date. Security software has to be used to perform regular system scans and to remove threats and issues. If your computer is already infected with 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate this malware.
Screenshot of 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware's process on Windows Task Manager ("AutoIt v3 Script (32 bit)" process name):
Screenshot of the "cracked" software website used to promote 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ?
- STEP 1. Uninstall 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ application using Control Panel.
- STEP 2. Remove 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ ads from Google Chrome.
- STEP 3. Remove 'Ads by 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ' from Mozilla Firefox.
- STEP 4. Remove 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ extension from Safari.
- STEP 5. Remove rogue plug-ins from Microsoft Edge.
89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ removal:
Windows 11 users:
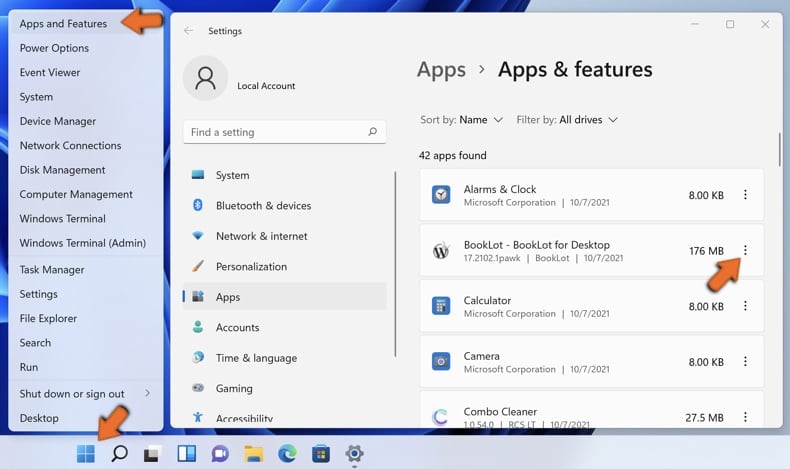
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall.
Windows 10 users:
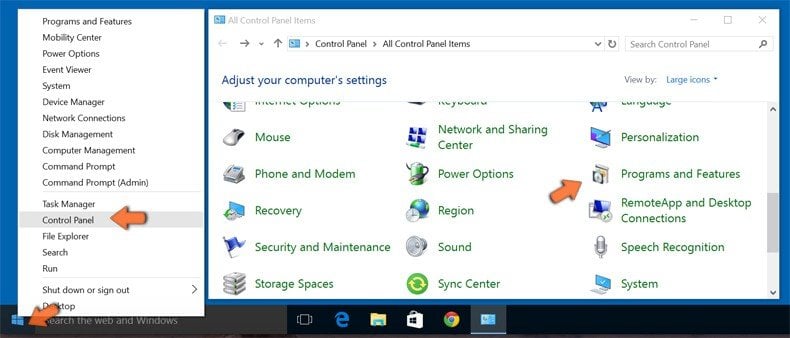
Right-click in the lower left corner of the screen, in the Quick Access Menu select Control Panel. In the opened window choose Programs and Features.
Windows 7 users:
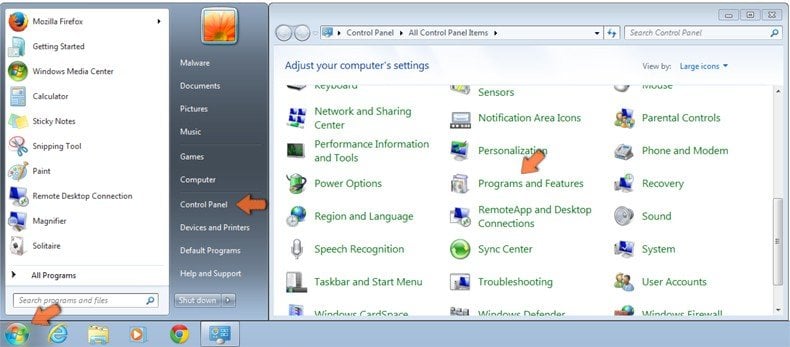
Click Start (Windows Logo at the bottom left corner of your desktop), choose Control Panel. Locate Programs and click Uninstall a program.
macOS (OSX) users:

Click Finder, in the opened screen select Applications. Drag the app from the Applications folder to the Trash (located in your Dock), then right click the Trash icon and select Empty Trash.
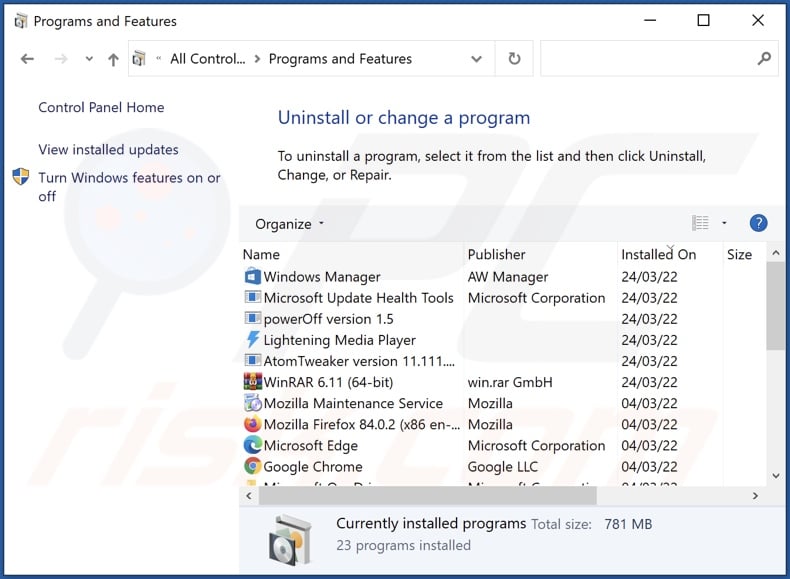
In the uninstall programs window, look for questionable applications, select these entries and click "Uninstall" or "Remove".
After uninstalling the potentially unwanted applications, scan your computer for any remaining unwanted components or possible malware infections. To scan your computer, use recommended malware removal software.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Remove rogue extensions from Internet browsers:
Video showing how to remove potentially unwanted browser add-ons:
 Remove malicious extensions from Google Chrome:
Remove malicious extensions from Google Chrome:
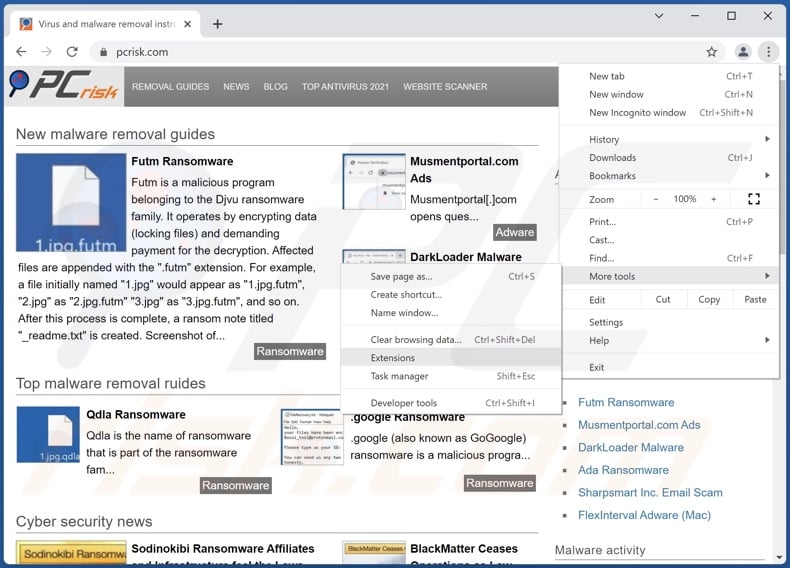
Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "More tools" and click "Extensions". Locate all questionable browser extensions and remove them.
(at the top right corner of Google Chrome), select "More tools" and click "Extensions". Locate all questionable browser extensions and remove them.
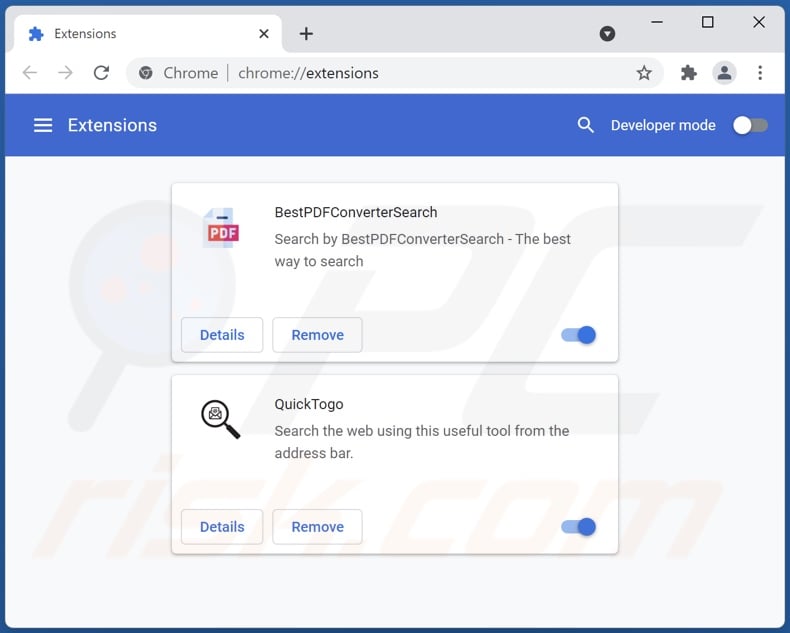
Optional method:
If you continue to have problems with removal of the 89n3pdyzzakoh7w6n8zrjgddktjh8iwfg6ekrvi3kvpq clipboard hijacker, reset your Google Chrome browser settings. Click the Chrome menu icon ![]() (at the top right corner of Google Chrome) and select Settings. Scroll down to the bottom of the screen. Click the Advanced… link.
(at the top right corner of Google Chrome) and select Settings. Scroll down to the bottom of the screen. Click the Advanced… link.
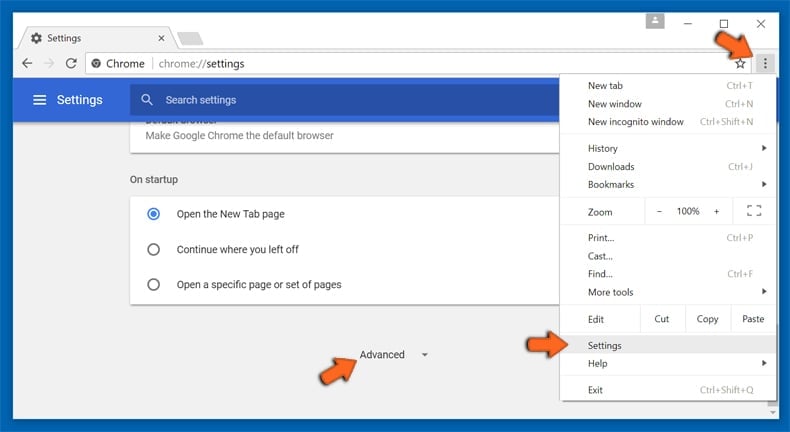
After scrolling to the bottom of the screen, click the Reset (Restore settings to their original defaults) button.
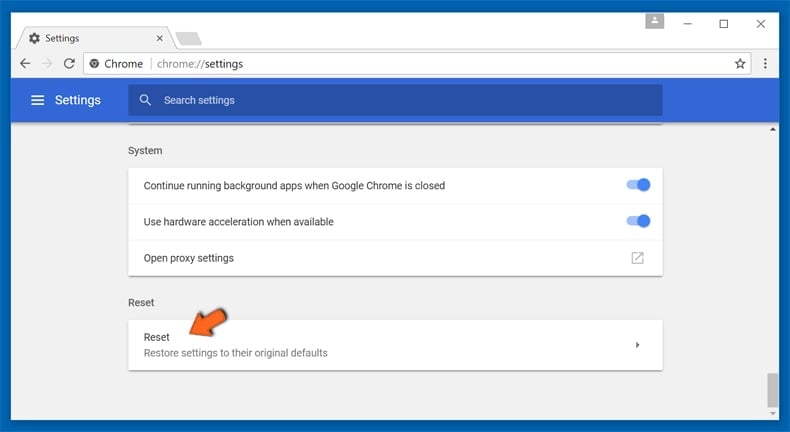
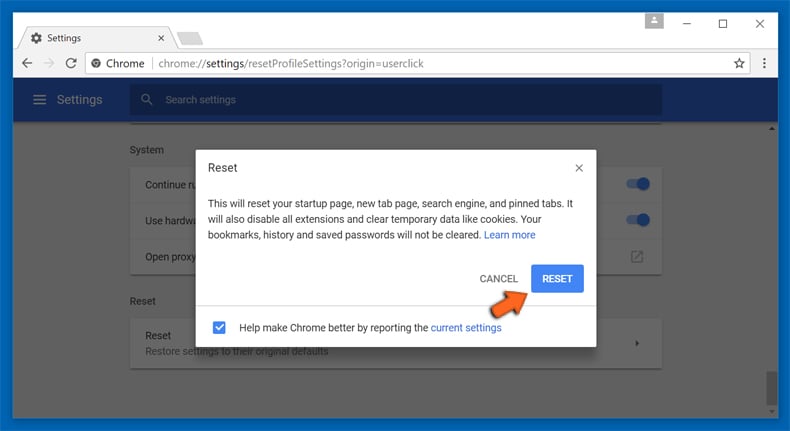
In the opened window, confirm that you wish to reset Google Chrome settings to default by clicking the Reset button.
 Remove malicious plugins from Mozilla Firefox:
Remove malicious plugins from Mozilla Firefox:
Click the Firefox menu ![]() (at the top right corner of the main window), select "Add-ons". Click "Extensions", in the opened window, remove all questionable browser extensions.
(at the top right corner of the main window), select "Add-ons". Click "Extensions", in the opened window, remove all questionable browser extensions.
Optional method:
Computer users who have problems with 89n3pdyzzakoh7w6n8zrjgddktjh8iwfg6ekrvi3kvpq clipboard hijacker removal can reset their Mozilla Firefox settings.
Open Mozilla Firefox, at the top right corner of the main window, click the Firefox menu, ![]() in the opened menu, click Help.
in the opened menu, click Help.
Select Troubleshooting Information.
In the opened window, click the Refresh Firefox button.
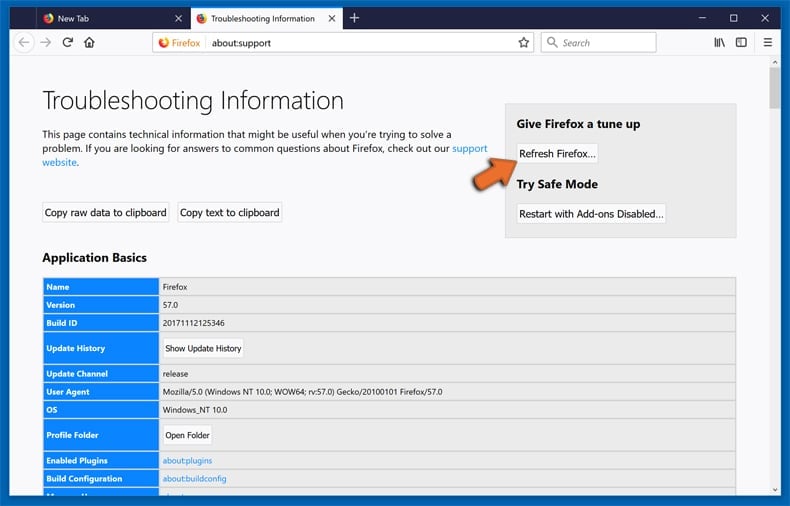
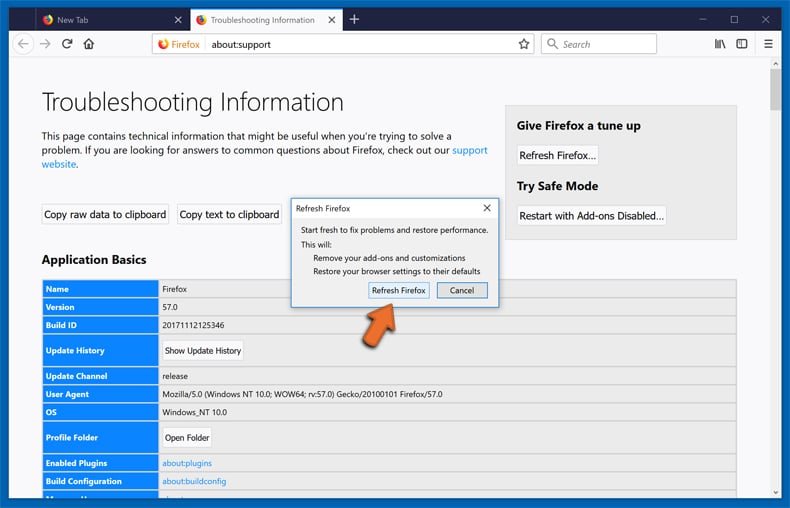
In the opened window, confirm that you wish to reset Mozilla Firefox settings to default by clicking the Refresh Firefox button.
 Remove malicious extensions from Safari:
Remove malicious extensions from Safari:
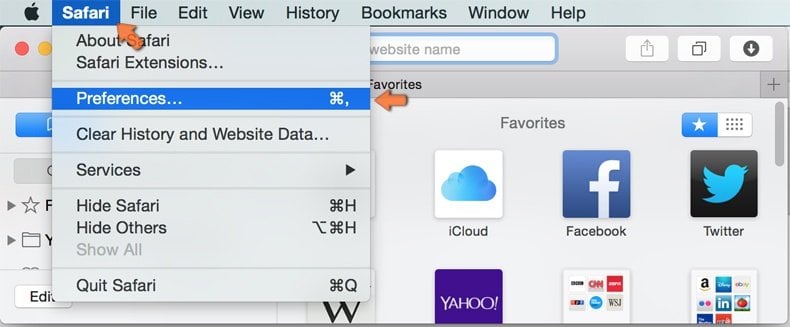
Make sure your Safari browser is active, click Safari menu, and select Preferences....
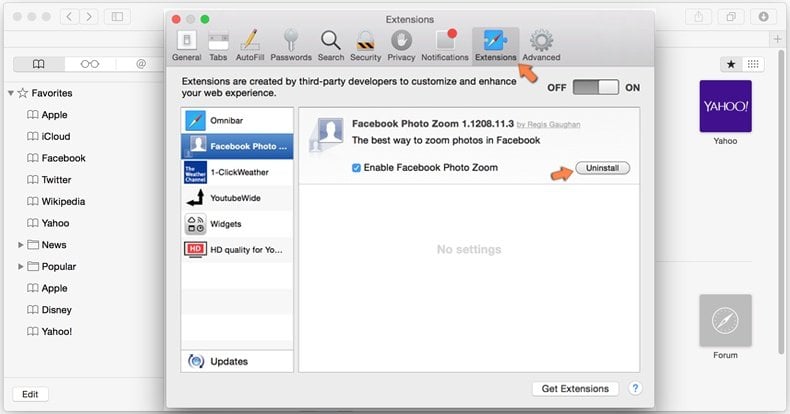
In the opened window click Extensions, locate any recently installed suspicious extension, select it and click Uninstall.
Optional method:
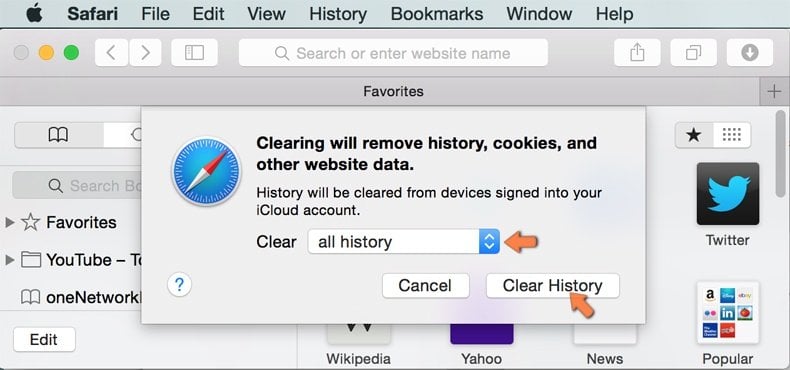
Make sure your Safari browser is active and click on Safari menu. From the drop down menu select Clear History and Website Data...
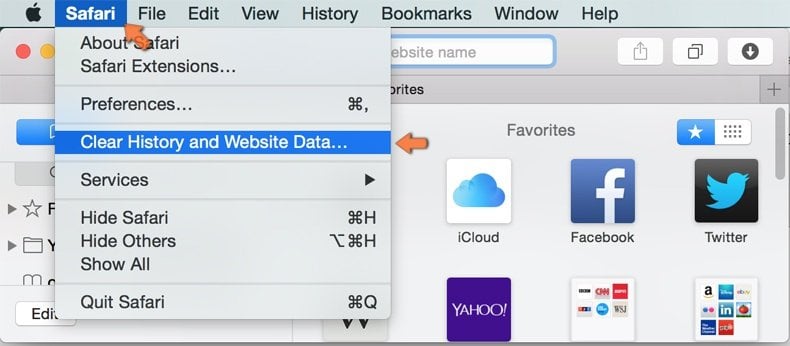
In the opened window select all history and click the Clear History button.
 Remove malicious extensions from Microsoft Edge:
Remove malicious extensions from Microsoft Edge:
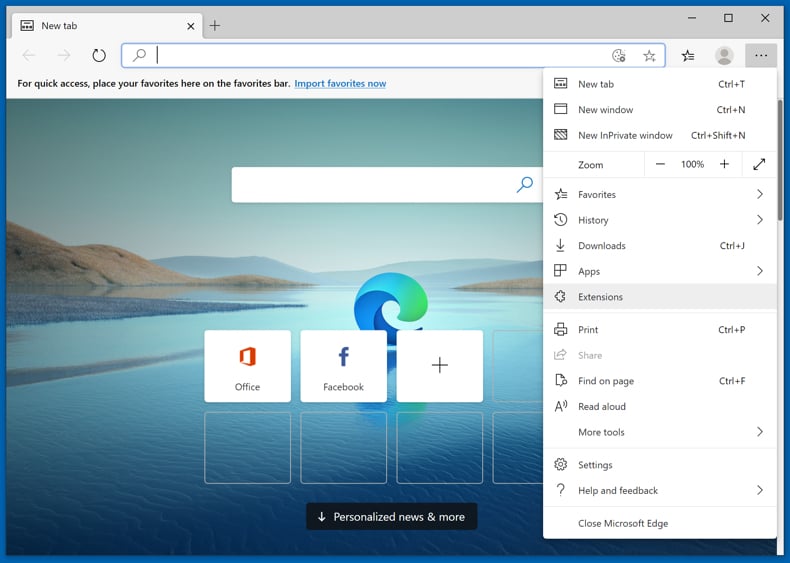
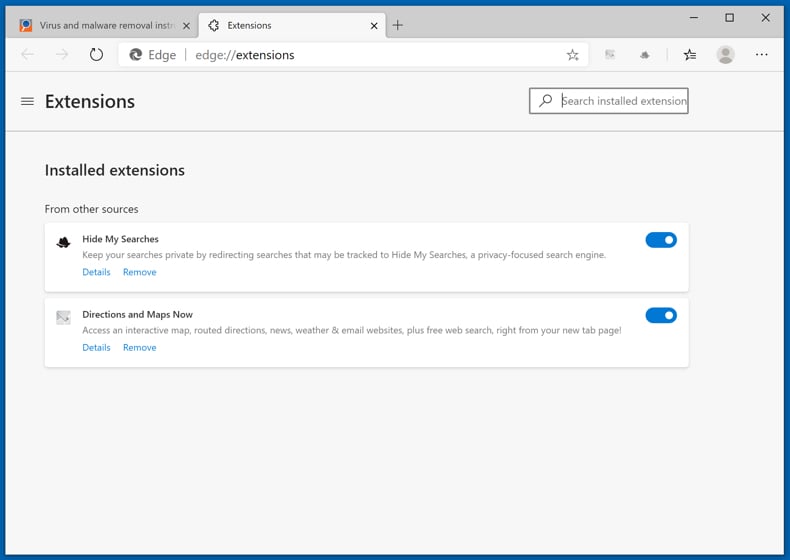
Click the Edge menu icon ![]() (at the upper-right corner of Microsoft Edge), select "Extensions". Locate all recently-installed suspicious browser add-ons and click "Remove" below their names.
(at the upper-right corner of Microsoft Edge), select "Extensions". Locate all recently-installed suspicious browser add-ons and click "Remove" below their names.
Optional method:
If you continue to have problems with removal of the 89n3pdyzzakoh7w6n8zrjgddktjh8iwfg6ekrvi3kvpq clipboard hijacker, reset your Microsoft Edge browser settings. Click the Edge menu icon ![]() (at the top right corner of Microsoft Edge) and select Settings.
(at the top right corner of Microsoft Edge) and select Settings.
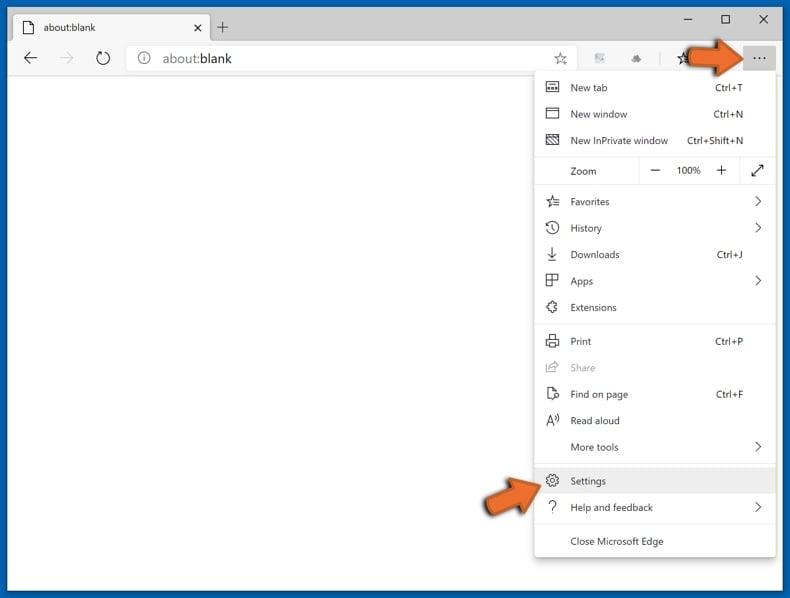
In the opened settings menu select Reset settings.
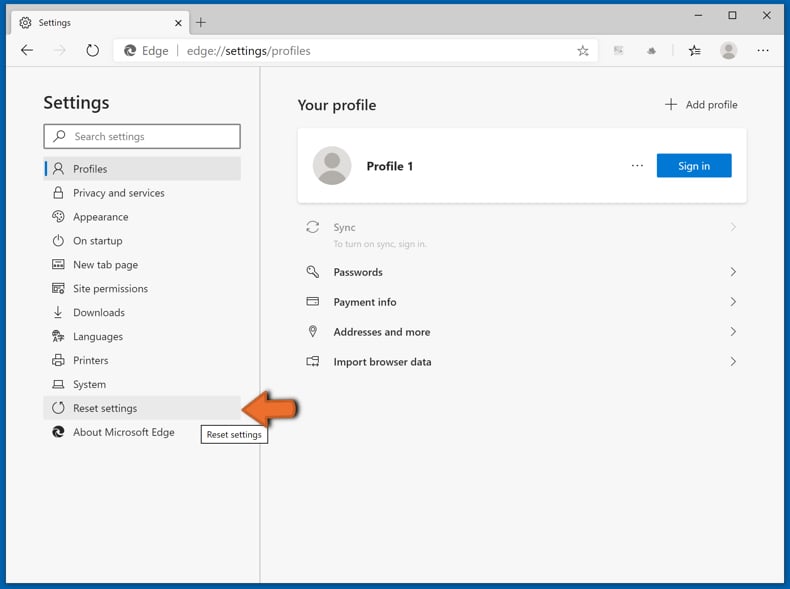
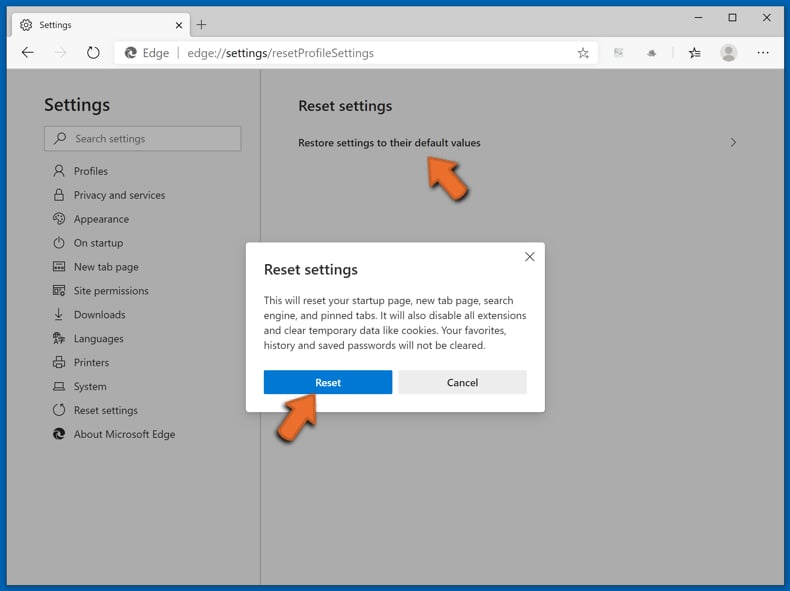
Select Restore settings to their default values. In the opened window, confirm that you wish to reset Microsoft Edge settings to default by clicking the Reset button.
- If this did not help, follow these alternative instructions explaining how to reset the Microsoft Edge browser.
Frequently Asked Questions (FAQ)
My computer is infected with 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware, should I format my storage device to get rid of it?
No, such drastic measures are absolutely unnecessary for the removal of this malicious program.
What are the biggest issues that 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware can cause?
The threats a piece of malicious software poses depends on its abilities and the cyber criminals' modus operandi. This clipboard hijacker was intended to replace the addresses of cryptowallets (copied into the clipboard) with one owned by the criminals - during outgoing cryptocurrency transactions, thereby transferring the funds to the attackers. However, this malicious program does not detect when such a transaction is being made and pastes the address regardless of the copied information. Hence, victims are far more likely to notice this rogue behavior and not make any cryptocurrency transactions.
What is the purpose of 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware?
As described in the previous answer, this clipboard hijacker is intended to reroute outgoing cryptocurrency transactions. Therefore, this malware aims to generate revenue at victims' expense. However, it is unlikely for this malicious program to achieve its goals due to its flaws.
How did 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ malware infiltrate my computer?
We discovered 89N3PDyZzakoH7W6n8ZrjGDDktjh8iWFG6eKRvi3kvpQ bundled into an installer that we downloaded from a website offering "cracked" software. However, malware is distributed using a wide variety of dubious techniques, e.g., drive-by downloads, spam mail, online scams, freeware and third-party download sites, Peer-to-Peer sharing networks, illegal software activation tools ("cracks"), fake updates, and so on. Some malicious programs can self-proliferate through local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner is capable of detecting and eliminating nearly all known malware infections. However, it must be emphasized that running a full system scan is key - since high-end malicious programs tend to hide deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion