How to remove BrowserVenom malware from the operating system
TrojanAlso Known As: BrowserVenom proxyware
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of malware is BrowserVenom?
BrowserVenom is a piece of malicious software that operates as proxyware. It manipulates users' network traffic and gathers vulnerable information.
BrowserVenom was proliferated under the guise of DeepSeek. Evidence found within the infrastructure promoting the fake app suggests that it was created (and possibly used) by Russian-speaking cyber criminals. The scope of this campaign is likely worldwide, but large numbers of infections were detected in Cuba, Brazil, Mexico, Egypt, the Republic of South Africa, Nepal, and India.

BrowserVenom malware overview
BrowserVenom has been observed infiltrating systems through a multi-stage chain. In the first stage, users can be presented with a decoy – a fake Cloudflare CAPTCHA test ("I am not a robot"). After its completion, another window is displayed – options for installing the fake DeekSeek together with Ollama or LM studio (both likewise fraudulent offers). Selecting either of the "Install" buttons initiates the next stage, which culminates in the infiltration of BrowserVenom.
This malware has anti-detection capabilities, i.e., it attempts to add itself as an exclusion for the Microsoft Defender Antivirus. The success depends on whether the user has admin privileges on the system.
BrowserVenom functions as proxyware. This malware modifies browsing instances to force the Internet traffic through a proxy controlled by the attackers – thus, they can manipulate the network traffic and collect sensitive data. To elaborate on how BrowserVenom carries out this activity, on Chromium-based browsers – it adds a proxy-server argument and alters existing LNK (Windows shortcut) files, and for Gecko-based browsers – it modifies the user's profile preferences.
BrowserVenom may be used for a variety of nefarious purposes in addition to monitoring browsing activity and gathering associated information. In general, proxyware can be utilized to register numerous social media and other online accounts (for spam, scam, or malware-spreading purposes), to scour highly sensitive websites that host private data (e.g., governmental, judiciary, etc.), sneakily click ads (affiliate scam purposes), visit malware-distributing sites, and so on.
Additionally, BrowserVenom has the ability to download content (like binaries) from the Web. Hence, this malicious software may cause further system infections. At the time of research, no binary could be downloaded from the hardcoded domain. Yet this could be rectified in potential future releases of this proxyware, which is quite likely since malware developers often improve upon their software and methodologies.
To summarize, the presence of malware like BrowserVenom on devices can lead to multiple system infections, severe privacy issues, financial losses, and identity theft.
| Name | BrowserVenom proxyware |
| Threat Type | Trojan, proxyware. |
| Detection Names | Jiangmin (Trojan.Selfdel.vfn), Kaspersky (HEUR:Trojan.Win32.SelfDel.gen), VBA32 (Trojan.SelfDel), Full List Of Detections (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Malware in general
Malware is a broad term covering programs with a variety of malicious functionalities. Some prevalent types include loaders that cause chain infections, stealers that extract/exfiltrate data, ransomware that encrypts files to demand ransoms for their decryption, and many, many others.
Furthermore, malware is not limited to its classification, i.e., it may possess various differing capabilities. What is more, malware infections can be complex and involve multiple malicious programs.
We have written thousands of articles on malware; Dispout, Taskbarify, Viewndown – are some of our newest on programs with proxyware abilities, TetraLoader, NETXLOADER, TransferLoader – on loaders, EDDIESTEALER, Octalyn, Katz – on stealers, and Puld, Backups, SafeLocker – on ransomware.
It must be emphasized that regardless of how malware operates – its presence on a system endangers device and user safety. Therefore, all threats must be removed immediately upon detection.
How did BrowserVenom infiltrate my computer?
BrowserVenom has been distributed under the guise of the DeepSeek application. The malicious webpage spreading this malware as the DeepSeek-R1 LLM environment installer imitated the official DeepSeek website. This fake page was endorsed by abusing Google Ads to display it as the topmost result on search engines (malvertising).
It is pertinent to mention that older campaigns proliferating other malware with a DeepSeek disguise have been promoted via social media spam on X (more commonly referred to by its former name – Twitter).
Other distribution techniques are possible. Generally, malware is spread by relying on phishing and social engineering tactics. Malicious programs are often disguised as or bundled with genuine or legitimate-sounding software/media.
Infectious files can be archives (RAR, ZIP, etc.), executables (.exe, .run, etc.), documents (Microsoft Office, Microsoft OneNote, PDF, etc.), JavaScript, and so forth. Merely opening a malicious file can be enough to trigger the infection chain.
The most prevalent distribution methods include: malvertising, attachments/links in spam (e.g., emails, PMs/DMs, social media posts, etc.), online scams, trojans (backdoors/loaders), drive-by (stealthy/deceptive) downloads, suspicious download sources (e.g., freeware and third-party sites, P2P sharing networks, etc.), pirated content, illegal software activation tools ("cracks"), and fake updates.
Some malicious programs can even self-spread through local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
How to avoid installation of malware?
Caution is critical to ensuring device integrity and user safety. Therefore, always be vigilant when browsing, as the Internet is full of deceptive and malicious content. Treat incoming emails and other messages with care. Do not open attachments or links found in dubious/irrelevant mail, as they can be virulent.
Additionally, download only from official and trustworthy channels. Activate and update software using functions/tools provided by legitimate developers, as those obtained from third-parties can contain malware.
It is paramount to have a reputable antivirus installed and kept updated. Security software must be used to run regular system scans and to remove detected threats/issues. If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Screenshot of the fake DeepSeek website distributing BrowserVenom (image source – Securelist):

Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is BrowserVenom?
- STEP 1. Manual removal of BrowserVenom malware.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
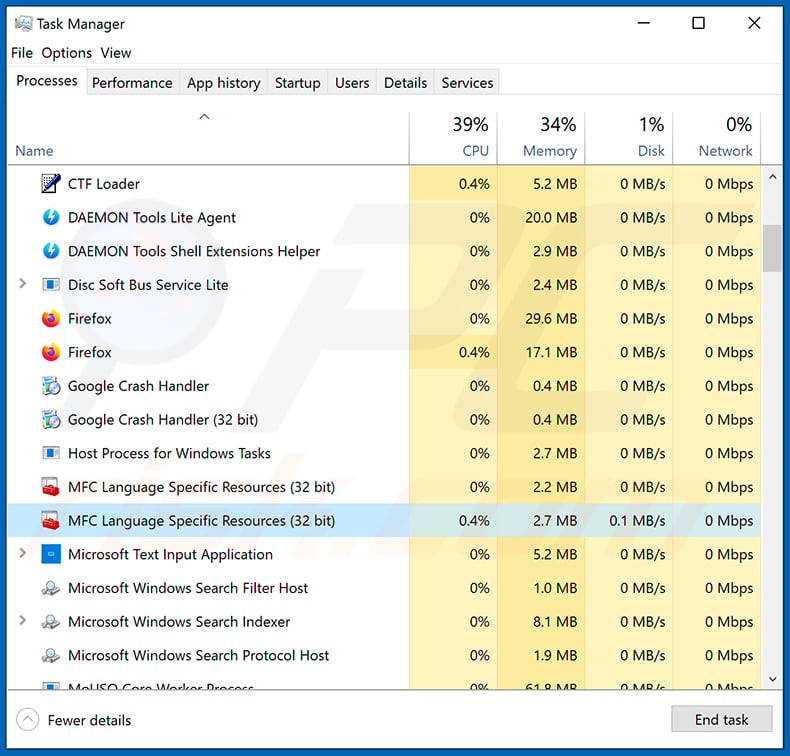
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
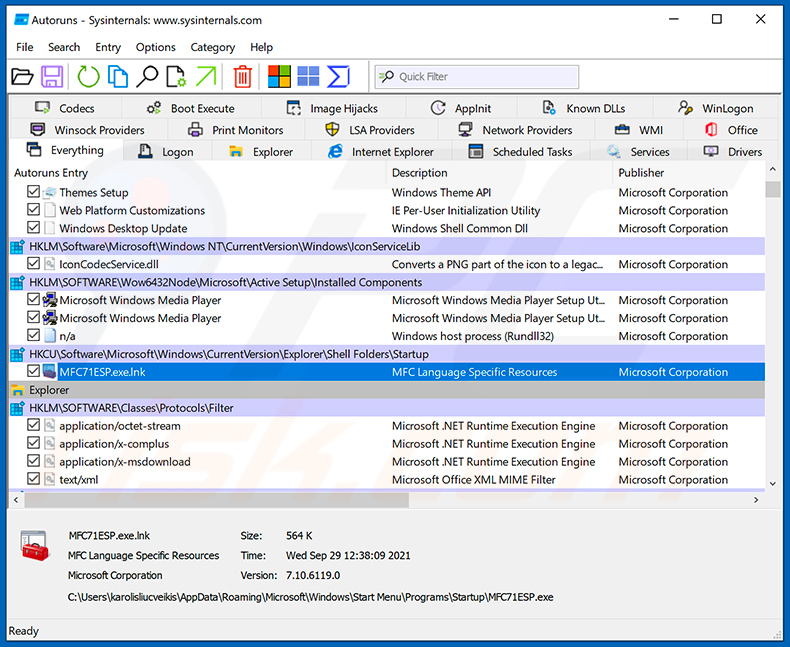
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
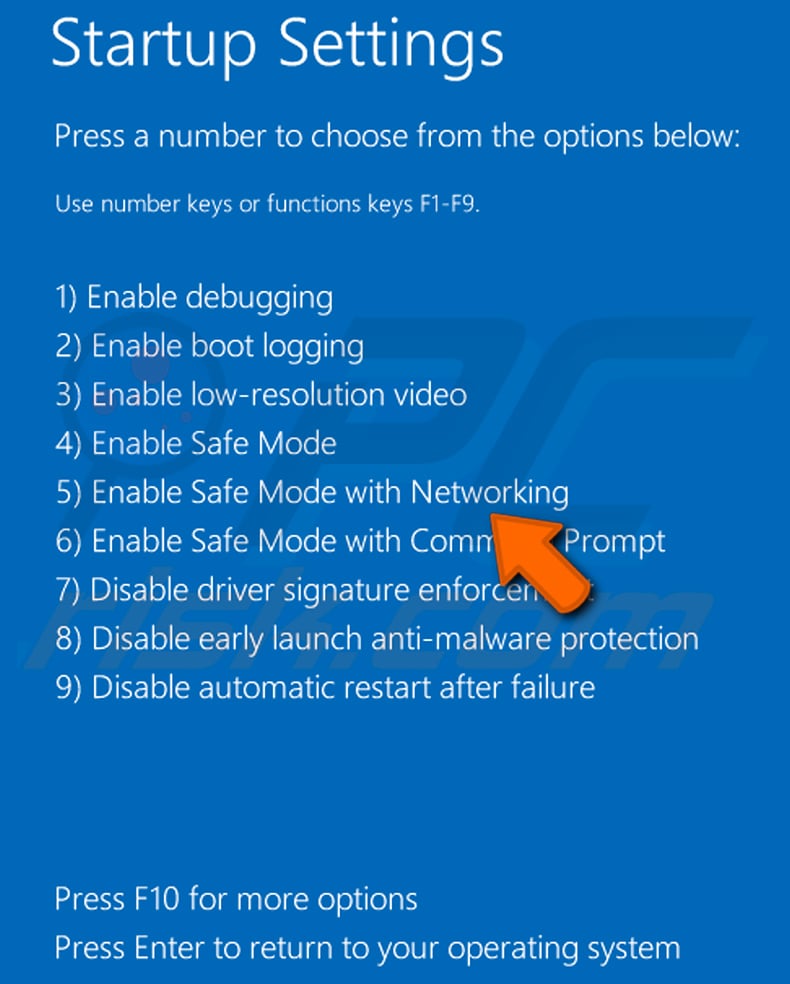
Video showing how to start Windows 10 in "Safe Mode with Networking":
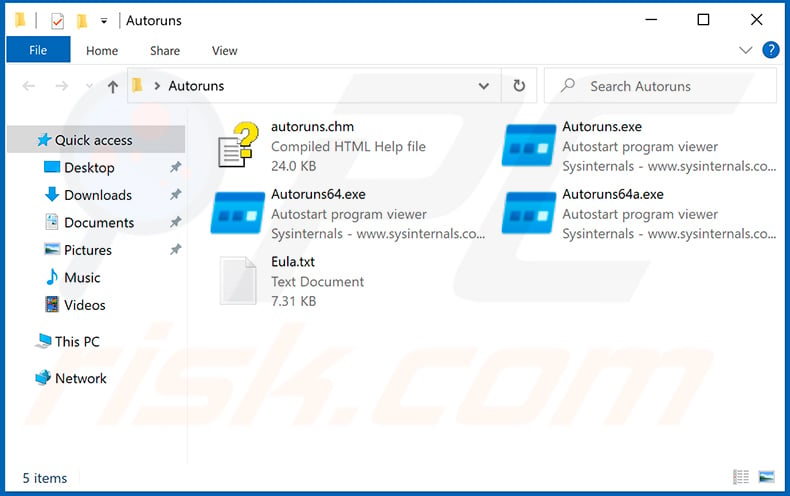
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
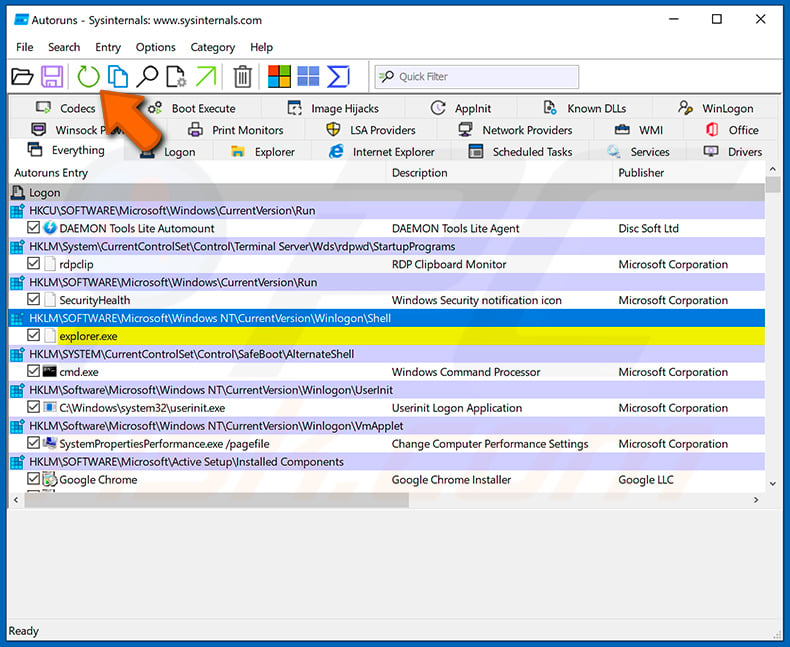
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
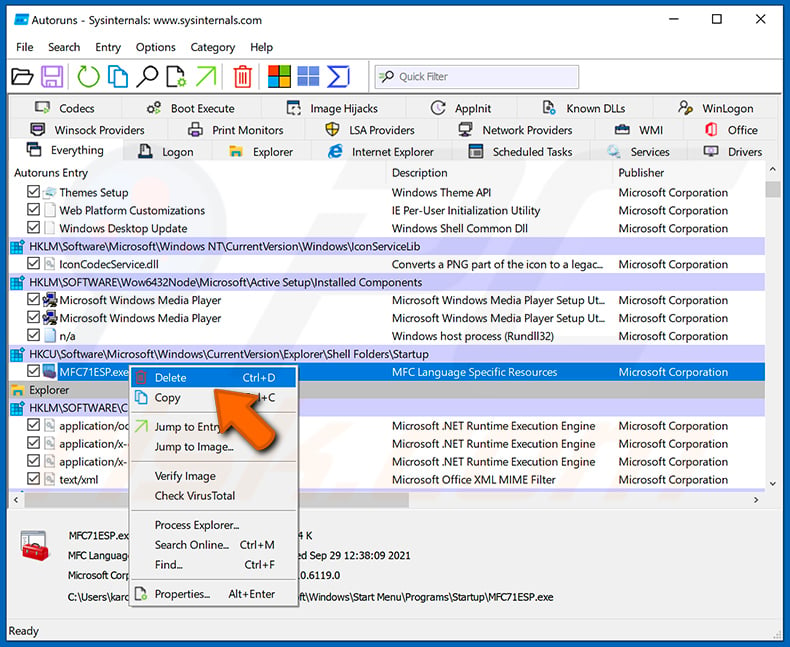
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
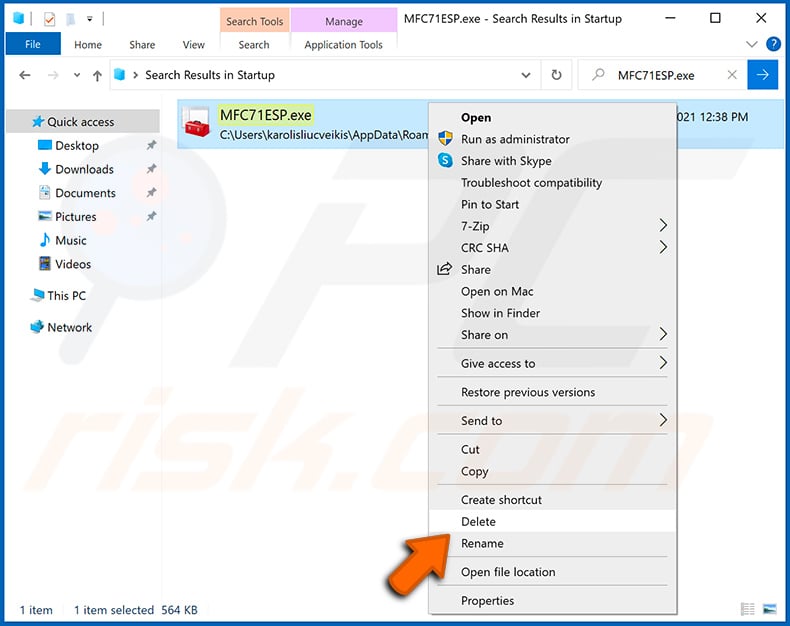
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with BrowserVenom malware, should I format my storage device to get rid of it?
Malware removal rarely requires such drastic measures.
What are the biggest issues that BrowserVenom malware can cause?
The dangers posed by an infection differ depending on the malware's functionalities and the cyber criminals' goals. BrowserVenom works as proxyware and may infiltrate additional malicious content into systems. Generally, the presence of such malicious software can result in multiple system infections, serious privacy issues, financial losses, and identity theft.
What is the purpose of BrowserVenom malware?
Cyber criminals mainly use malware to generate revenue. However, attackers may also use malicious programs to amuse themselves, carry out personal vendettas, disrupt processes (e.g., websites, services, etc.), engage in hacktivism, and launch politically/geopolitically motivated attacks.
How did BrowserVenom malware infiltrate my computer?
BrowserVenom has been spread through fake DeepSeek installers distributed by sites imitating the official website, which were promoted via malvertising. Other disguises or distribution techniques are not unlikely.
Generally, malware is proliferated through drive-by downloads, online scams, spam, trojans, dubious download channels (e.g., freeware and third-party sites, P2P sharing networks, etc.), pirated programs/media, illegal software activation tools ("cracks"), and fake updates. Furthermore, some malicious programs can self-spread via local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
Will Combo Cleaner protect me from malware?
Combo Cleaner is designed to scan devices and remove all kinds of threats. It is capable of detecting and eliminating most of the known malware infections. Remember that performing a complete system scan is crucial since high-end malicious software typically hides deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion